2024数据安全产业人才积分争夺赛|Writeup
次阅读
6 min read
更新一下大家比较关心的题目🤤
重要的System32
给了整个Windows的System32的目录,大概率就是审计事件日志、注册表。翻了一坤年注册表,最后看到打印机存在一个flag相关的记录。
/重要的System32/System32/winevt/Logs/Microsoft-Windows-PrintService%4Operational.evtx
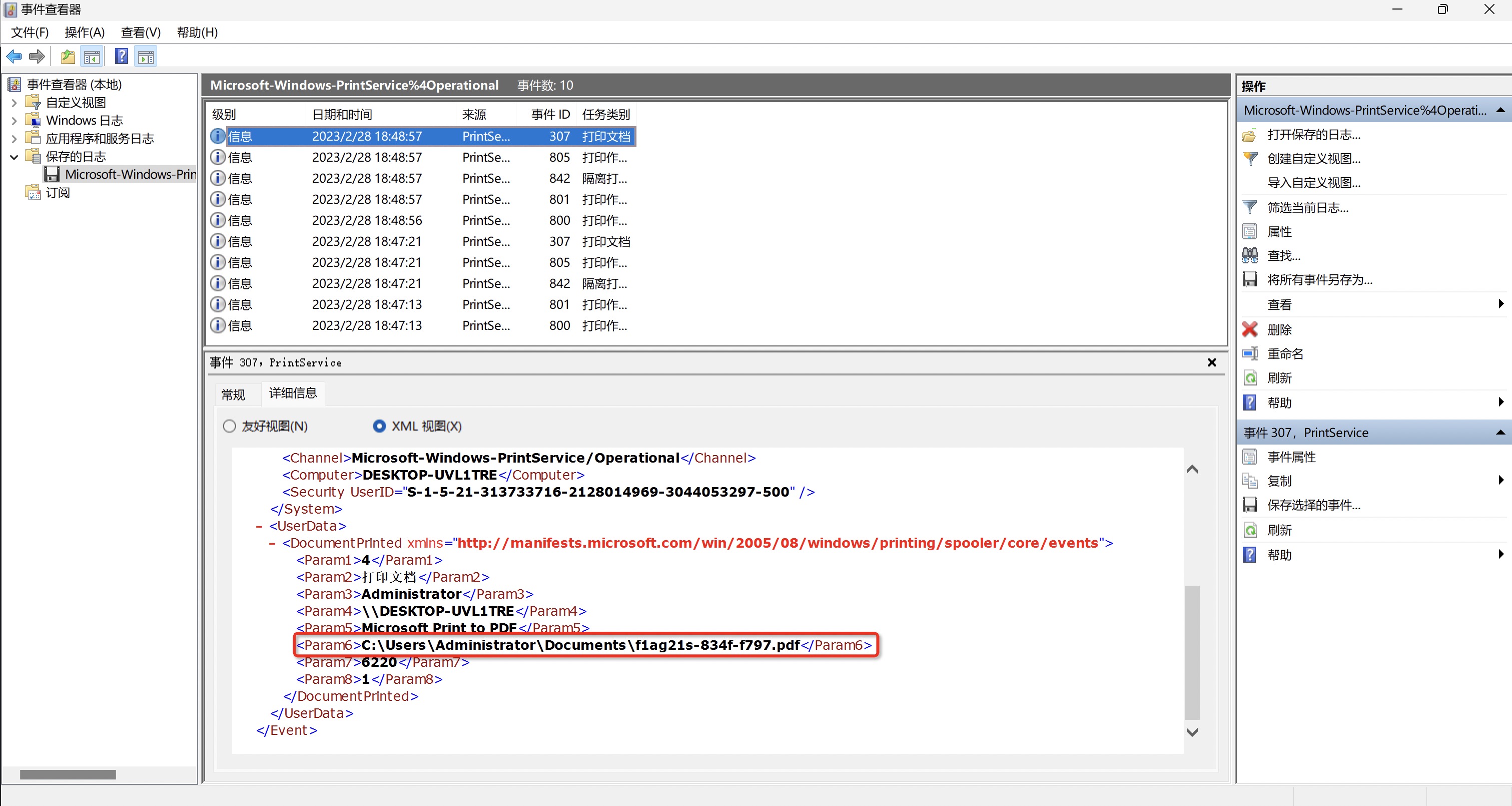
可以看到打印了一个flag的PDF文件,得到部分-834f-f797
再找一下这个文件存在哪,搜索得知wbem目录下存放着相关配置和信息。又翻了一坤年文件,在OBJECTS.DATA文件中看到了flag信息。
/重要的System32/System32/wbem/Repository/OBJECTS.DATA

拿到了一部分F1@43_is_{ef63fcbc-3467
接下来继续翻啊翻🤮
最终在注册表中找到一段信息,包含flag和Pwd
/重要的System32/System32/config/RegBack/HKEY_CURRENT_USER.reg
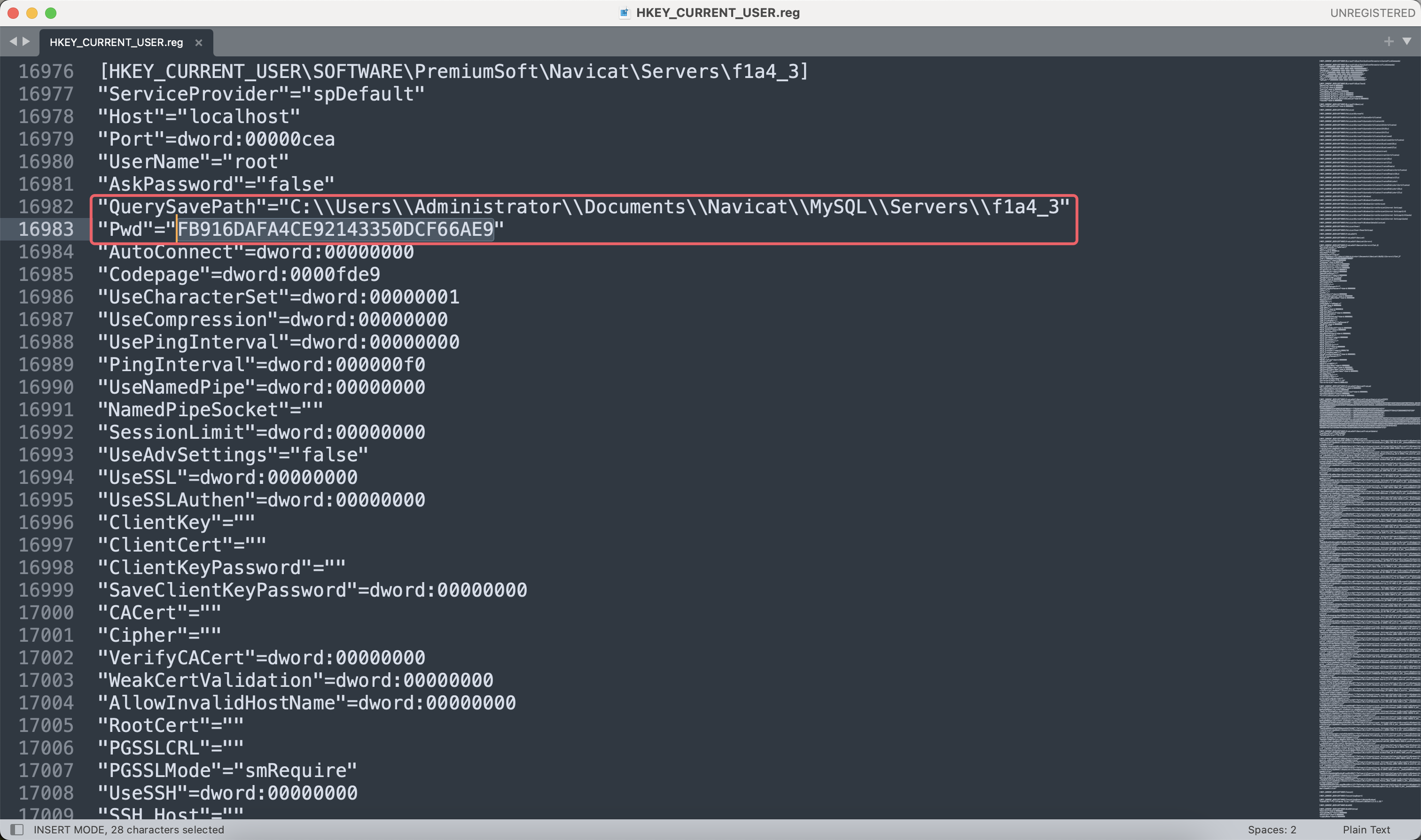
现在需要解密如下信息:
"QuerySavePath"="C:\\Users\\Administrator\\Documents\\Navicat\\MySQL\\Servers\\f1a4_3"
"Pwd"="FB916DAFA4CE92143350DCF66AE9"
目录中可以看到是Navicat连接MySQL的信息,所以搜一下相关的加密算法,最终找到一个合适的项目。
#!/usr/bin/env python3
import sys
from Crypto.Hash import SHA1
from Crypto.Cipher import AES, Blowfish
from Crypto.Util import strxor, Padding
class Navicat11Crypto:
def __init__(self, Key = b'3DC5CA39'):
self._Key = SHA1.new(Key).digest()
self._Cipher = Blowfish.new(self._Key, Blowfish.MODE_ECB)
self._IV = self._Cipher.encrypt(b'\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF')
def EncryptString(self, s : str):
if type(s) != str:
raise TypeError('Parameter s must be a str.')
else:
plaintext = s.encode('ascii')
ciphertext = b''
cv = self._IV
full_round, left_length = divmod(len(plaintext), 8)
for i in range(0, full_round * 8, 8):
t = strxor.strxor(plaintext[i:i + 8], cv)
t = self._Cipher.encrypt(t)
cv = strxor.strxor(cv, t)
ciphertext += t
if left_length != 0:
cv = self._Cipher.encrypt(cv)
ciphertext += strxor.strxor(plaintext[8 * full_round:], cv[:left_length])
return ciphertext.hex().upper()
def DecryptString(self, s : str):
if type(s) != str:
raise TypeError('Parameter s must be str.')
else:
plaintext = b''
ciphertext = bytes.fromhex(s)
cv = self._IV
full_round, left_length = divmod(len(ciphertext), 8)
for i in range(0, full_round * 8, 8):
t = self._Cipher.decrypt(ciphertext[i:i + 8])
t = strxor.strxor(t, cv)
plaintext += t
cv = strxor.strxor(cv, ciphertext[i:i + 8])
if left_length != 0:
cv = self._Cipher.encrypt(cv)
plaintext += strxor.strxor(ciphertext[8 * full_round:], cv[:left_length])
return plaintext.decode('ascii')
class Navicat12Crypto(Navicat11Crypto):
def __init__(self):
super().__init__()
def EncryptStringForNCX(self, s : str):
cipher = AES.new(b'libcckeylibcckey', AES.MODE_CBC, iv = b'libcciv libcciv ')
padded_plaintext = Padding.pad(s.encode('ascii'), AES.block_size, style = 'pkcs7')
return cipher.encrypt(padded_plaintext).hex().upper()
def DecryptStringForNCX(self, s : str):
cipher = AES.new(b'libcckeylibcckey', AES.MODE_CBC, iv = b'libcciv libcciv ')
padded_plaintext = cipher.decrypt(bytes.fromhex(s))
return Padding.unpad(padded_plaintext, AES.block_size, style = 'pkcs7').decode('ascii')
if __name__ == '__main__':
def Help():
print('Usage:')
print(' NavicatCrypto.py <enc|dec> [-ncx] <plaintext|ciphertext>')
print('')
print(' <enc|dec> "enc" for encryption, "dec" for decryption.')
print(' This parameter must be specified.')
print('')
print(' [-ncx] Indicate that plaintext/ciphertext is')
print(' prepared for/exported from NCX file.')
print(' This parameter is optional.')
print('')
print(' <plaintext|ciphertext> Plaintext string or ciphertext string.')
print(' NOTICE: Ciphertext string must be a hex string.')
print(' This parameter must be specified.')
print('')
def Main(argc : int, argv : list):
if argc == 3:
if argv[1].lower() == 'enc':
print(Navicat11Crypto().EncryptString(argv[2]))
elif argv[1].lower() == 'dec':
print(Navicat11Crypto().DecryptString(argv[2]))
else:
Help()
return -1
elif argc == 4:
if argv[1].lower() == 'enc' and argv[2].lower() == '-ncx':
print(Navicat12Crypto().EncryptStringForNCX(argv[3]))
elif argv[1].lower() == 'dec' and argv[2].lower() == '-ncx':
print(Navicat12Crypto().DecryptStringForNCX(argv[3]))
else:
Help()
return -1
else:
Help()
return 0
exit(Main(len(sys.argv), sys.argv))
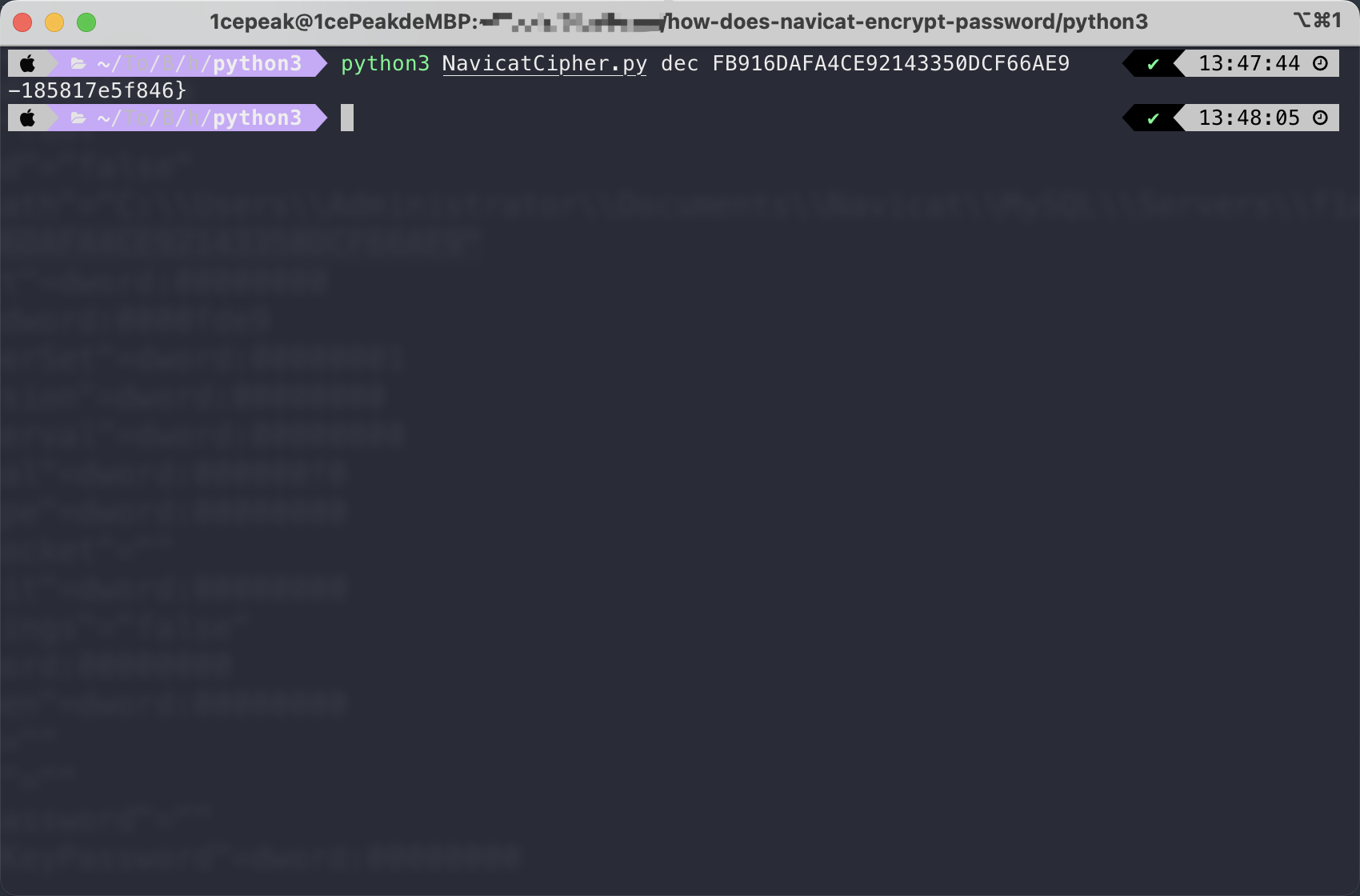
得到的结果是-185817e5f846}
所以这道题完整的flag是flag{ef63fcbc-3467-834f-f797-185817e5f846}
Strangesystem
Wireshark打开之后可以看到传了一张png
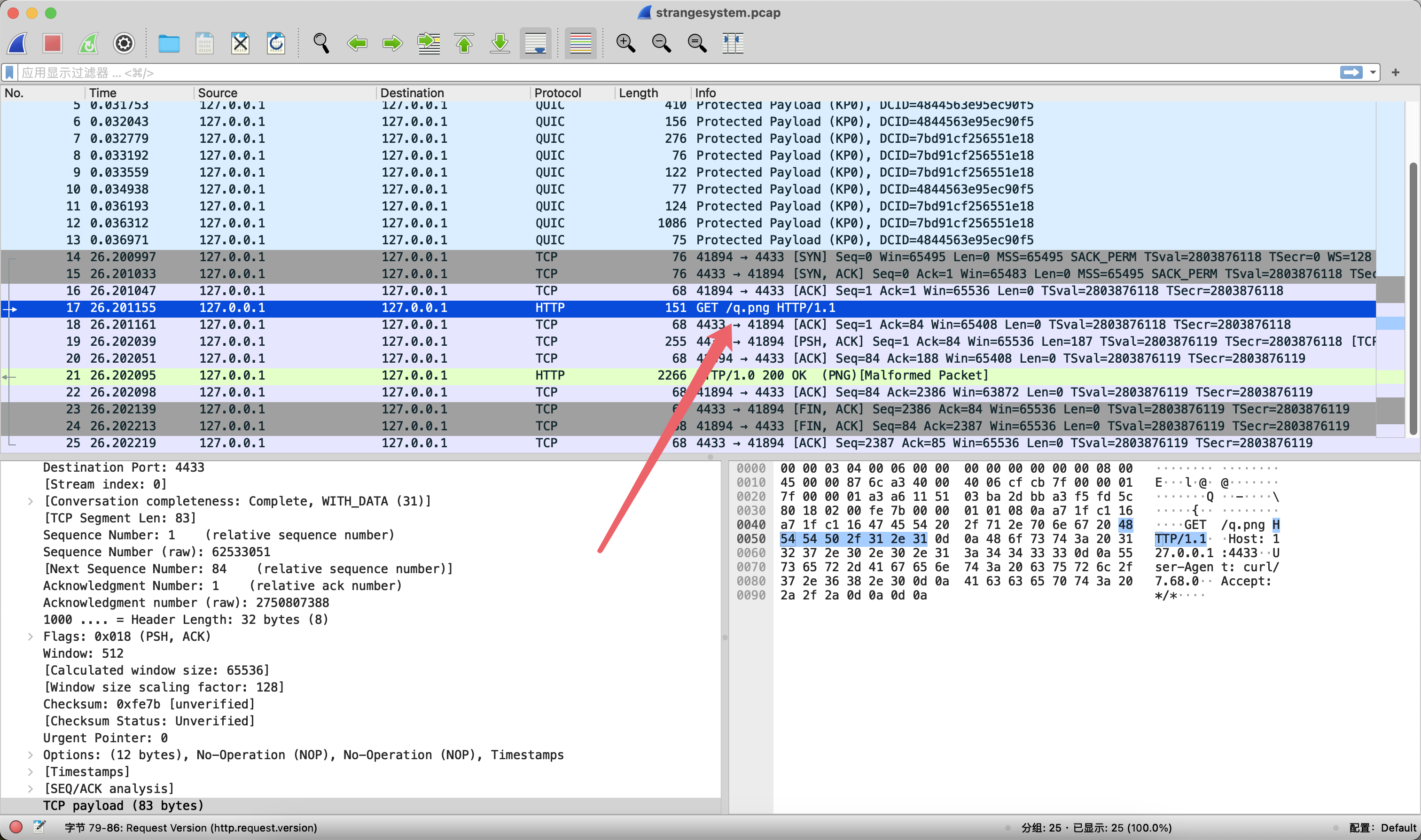
把这张图片导出来之后在末尾处可以看到有一个压缩包和TLS握手的信息

SERVER_HANDSHAKE_TRAFFIC_SECRET e8ef73b91b4c9d6e37113bcc88465a7f61badb5fd87177ca51c24ceab944b34a 82ec3ebf3131b2442d165bb00dd6b8d1a6b4c866daf3fd373c22d33886290ed2868a7395e691980b990de46b76a54f9e
CLIENT_HANDSHAKE_TRAFFIC_SECRET e8ef73b91b4c9d6e37113bcc88465a7f61badb5fd87177ca51c24ceab944b34a 10965df426257a285c6e812ed54468c59437e77bceff2c3a6d633dacefadf8188e97c4935df6815e5398b24273addc79
SERVER_TRAFFIC_SECRET_0 e8ef73b91b4c9d6e37113bcc88465a7f61badb5fd87177ca51c24ceab944b34a cdbf7c7a161af7aa829b14becaa2c000b8183000983e06589fef0c50e9462cf71aeb487e1cb1defaef06a941234ea7a2
CLIENT_TRAFFIC_SECRET_0 e8ef73b91b4c9d6e37113bcc88465a7f61badb5fd87177ca51c24ceab944b34a e58e4088a7840d3991ac2336c581d2a35edbebfd14420a29c287444c3631dc98038b71f1d153cd37ba46164145a028fd
将这些信息保存为文件导入Wireshark:

之后就可以看到明文信息了,直接追踪QUIC数据流。
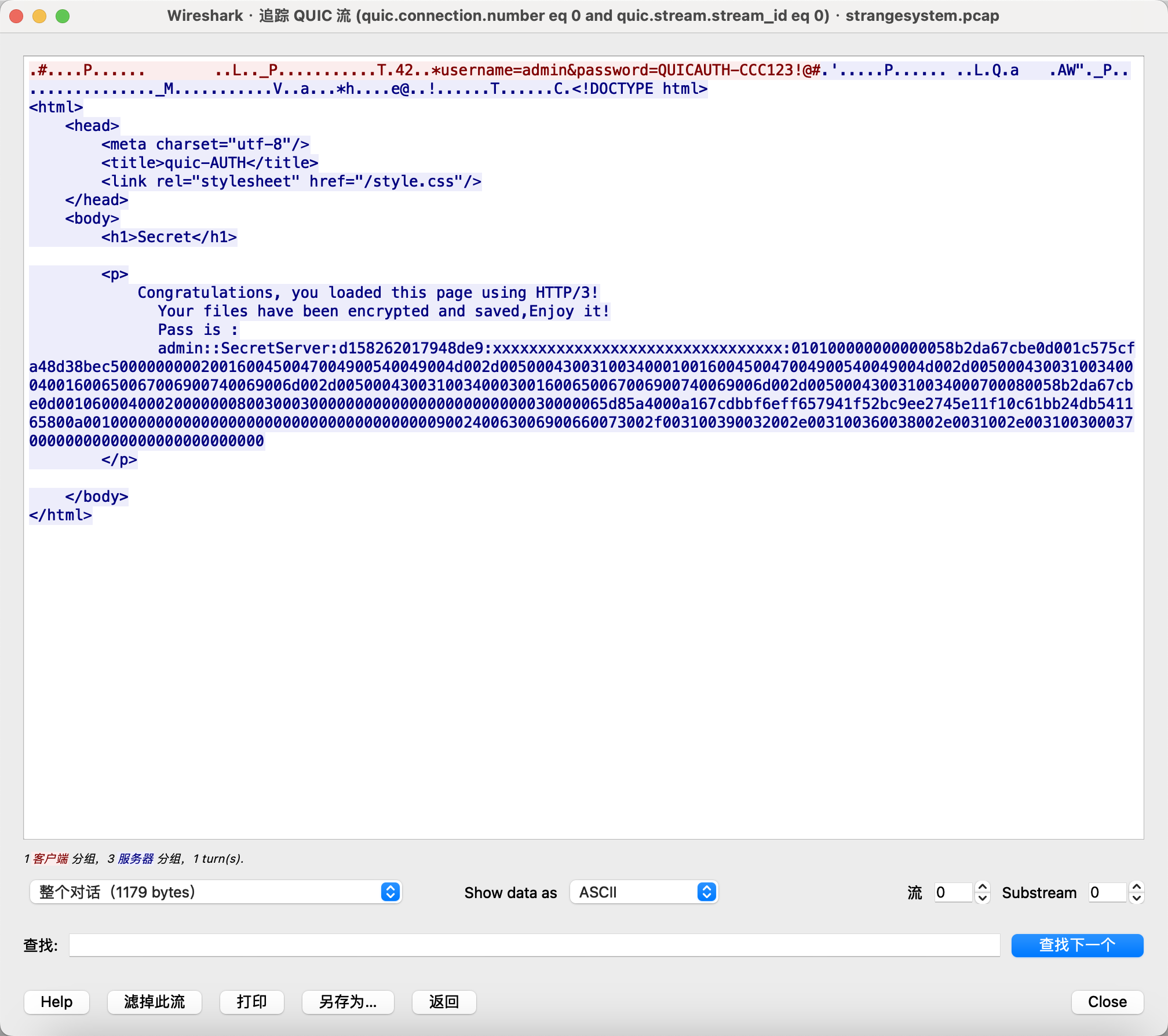
可以得到username=admin&password=QUICAUTH-CCC123!@#和一个html页面
<html>
<head>
<meta charset="utf-8"/>
<title>quic-AUTH</title>
<link rel="stylesheet" href="/style.css"/>
</head>
<body>
<h1>Secret</h1>
<p>
Congratulations, you loaded this page using HTTP/3!
Your files have been encrypted and saved,Enjoy it!
Pass is :
admin::SecretServer:d158262017948de9:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx:010100000000000058b2da67cbe0d001c575cfa48d38bec50000000002001600450047004900540049004d002d00500043003100340001001600450047004900540049004d002d00500043003100340004001600650067006900740069006d002d00500043003100340003001600650067006900740069006d002d0050004300310034000700080058b2da67cbe0d0010600040002000000080030003000000000000000000000000030000065d85a4000a167cdbbf6eff657941f52bc9ee2745e11f10c61bb24db541165800a001000000000000000000000000000000000000900240063006900660073002f003100390032002e003100360038002e0031002e00310030003700000000000000000000000000
</p>
</body>
</html>
可以看到存在xxxx部分,我们先来了解一下NTLMv2的生成过程:

所以接下来,可以根据整个过程来计算未知的部分。
# -*- coding: utf-8 -*-
# @Author : 1cePeak
import hashlib
import hmac
_ntlm = hashlib.new("md4", "QUICAUTH-CCC123!@#".encode("utf-16-le")).digest()
ntlm = _ntlm.hex()
print("NTLM:", ntlm)
user_domain_name = 'ADMINSECRETSERVER'.encode("utf-16-le")
firstHMAC = hmac.new(bytes.fromhex(ntlm), user_domain_name, hashlib.md5).hexdigest()
print("First HMAC:", firstHMAC)
ntlm_secret = "d158262017948de9010100000000000058b2da67cbe0d001c575cfa48d38bec50000000002001600450047004900540049004d002d00500043003100340001001600450047004900540049004d002d00500043003100340004001600650067006900740069006d002d00500043003100340003001600650067006900740069006d002d0050004300310034000700080058b2da67cbe0d0010600040002000000080030003000000000000000000000000030000065d85a4000a167cdbbf6eff657941f52bc9ee2745e11f10c61bb24db541165800a001000000000000000000000000000000000000900240063006900660073002f003100390032002e003100360038002e0031002e00310030003700000000000000000000000000"
Bytes_ntlm_secret = bytes.fromhex(ntlm_secret)
ntlmv2 = hmac.new(bytes.fromhex(firstHMAC), Bytes_ntlm_secret, hashlib.md5).hexdigest()
print("NTLMv2 hash:", ntlmv2)
得到的NTLMv2 hash是efa243f442b9d683eb1b00a2b1a0c9fc,用这个来解密压缩包就可以拿到flag{8af4d019-98ae-4b4f-a4e9-97076d205fd2}了。
完结,撒花🎉🎉🎉